David
G. Masse2
Andrew
D. Fernandes3
© 1996, 1997, 1999

| Economic
Modelling and Risk Management in Public Key Infrastratuctures1
David
G. Masse2
|
 |
| Text of a lecture given by the co-authors at the RSA Data Security Inc. annual conference held in San Francisco, California, on January 31, 1997. |
The Business Case for A Broadly-based Highly Scalable Public Key Infrastructure.
This is version 3.0 of this paper. This revision of April 15, 1997 updates references to the German Digital Signature Act in note 80. This paper was presented at the 1997 RSA Data Security Inc. annual symposium. The authors eventually intend to submit this paper for law review publication and they welcome the reader's comments. This paper was available before presentation and will remain available at least until law review publication at http://www.masse.org and will be continually updated to reflect the comments the authors receive. Persons providing comments are kindly asked to refer both to the version number of the paper and to the paragraph number to which the comment pertains.
Version 3.1 of February 21, 1999 updates author contact information, and references to the location of this document.
Version 3.2 of March 26, 2018 updates a link in footnote 87 to the MIT PGP server. Thank you to Sophie Hunt for pointing out the defective link.
[2] Internet as we now know it is merely the beginning of a new world-wide information infrastructure variously described as an Information Superhighway,5the I-Way, the National Information Infrastructure,6the Global Information Infrastructure,7etc., ad nauseam. Notwithstanding the unending stream of hyperbolic, clichéd public statements and media coverage concerning open networks and the information revolution they are spawning, the fact remains that open network technology holds the promise of a vastly changed world in which communications between human beings will reach a fundamentally new plateau. In an age where industry and governments everywhere struggle to reduce overheads and shrink budgets and yet need to continue to provide high levels of service to the public they serve, open networks probably hold the key to the future.
[3] In order to fulfill their promise, open networks must provide an efficient, highly scalable way to transmit quantities of information from point to point while doing so with a high degree of assurance. While the business community and the press are presently very nearly obsessed with the advent of large-scale retail commerce on the Internet, retail electronic commerce is only a small subset of the broader spectrum of 'commercial' traffic global open networks must one day carry. Open networks must offer a digital communications medium which matches the capability of its tangible, paper-based competitors before they can be expected to exceed those capabilities. Global transportation concerns like state-run postal services and privately owned enterprises like United Parcel Service and Federal Express do much more than act as conduits for retail commerce. They also serve an essential role in providing the messaging backbone for the services industry including the financial and accounting community, the legal and medical community, the architectural and engineering community, and so on. Retail and wholesale commerce is clearly but a small portion of the total communication pie.
[4] Commercial and professional analog voice communications have been travelling on the global telecom infrastructure for a very long time now. If at some point in the past the security and propriety of communicating sensitive information in this way was questioned, those questions have long since been put to rest. The introduction of widespread commercial data communications over the telecom infrastructure in the form of point to point data communications and facsimile transmissions has not, to date, given rise to much in the way of legal or social controversy as to the propriety of communicating in that fashion.
[5] Open networks, such as Internet, obey rules which differ quite materially from the traditional, switched, point to point telecom infrastructure with which we are now very familiar. Even though the telecom infrastructure is not extra-ordinarily secure and lends itself quite readily to both licit and illicit interception of traffic, we have come to terms with it and we accept that the medium it provides for our commercial communications is reasonably secure, at least as regards the vast bulk of both personal and commercial traffic with which we routinely entrust it. Open, packet-switched networks like Internet derive their extra-ordinary efficiency by minimizing the infrastructure needed to allow communications to occur. The network relies on its openness to achieve its ends: packets must be easily inspected by each node encountered on their trek across the wired and networked globe so that they can be handed off in the probable direction of their intended destination. This openness is generally recognized as providing a medium which is too insecure to permit digital commerce to flourish as it ought normally to do.
[6] In order to flourish, commerce requires a communications medium which is sufficiently secure, in relative terms, to assure both the integrity of the message and the authentication of its source and destination. The risk which commerce abhors grows in direct proportion to the degree to which the communications medium employed is perceived as relatively insecure. The greater the perceived inherent risk, the less commerce will tend to rely on the medium. Risk, and the absence of risk, is rarely absolute and is inherently relative. Human history gives example after example of mankind's genius in devising ever more secure media for commerce. That which is perceived today as offering a reasonable venue for commercial communication, becomes thoroughly unattractive with the advent of a new and improved way of doing business. No business concern in today's world would risk a valuable trans-Atlantic shipment of commodities in the hold of the staunchest ship of England's merchant fleet of 1697.
[7] At the present time, the business community relies without much, if any, concern on point to point voice communications over the telecom infrastructure. The needs of identification, integrity, confidentiality and authentication are met quite well. The switched nature of the telephone system performs most of the task both of ensuring the integrity and authenticity of our transmissions: the number assigned by the local telephone company authenticates the terminal end of the communication (i.e., for a single residential telephone line, the physical address at which the line terminates) and the voice of the person to whom we are speaking does the rest, as we verify the subtleties of tone, inflection and intonation of the speaker against the voice of the person we remember. The integrity and confidentiality of the message we hear is vouched for by the logical coherence of speech and our knowledge that (except for rural party lines - which still exist in the case of phones installed in many summer cottages) the interception of our conversation is technically somewhat difficult and is in fact quite unlikely.
[8] As the business community began to use the telecom infrastructure increasingly for data communications in the late 1970's, in large measure it transferred to its data communications the trust developed through long reliance on the telecom system for voice communication without giving much thought to the fundamental differences between voice and data communication. The source of our existing faith and trust in the integrity of the telecom infrastructure stems from our long collective experience in voice communications.
[9] In data communications however, the traditional authentication and verification tools we employ no longer work for us: our bits and bytes look and sound pretty much like everyone else's bits and bytes. We are able to verify that our message was received integrally in a point to point data communication by periodically transmitting data back to the sender for verification against the bits originally sent, but we have no way of knowing precisely who the reply is coming from. Thus, taking the most prevalent example of data communications failure, every day clerks in businesses all over the world transmit faxes to the wrong destination by inadvertently keying in the wrong telephone number. No one is the wiser until the intended recipient denies receiving the message. Even then, we assume that the machine failed in some way, rarely considering that the message is now in the wrong hands. Nevertheless, the risks inherent in point to point switched data communications have not generated much, if any, attention and concern.
[10] Open packet-switched networks are quite another kettle of fish however. In the case of the open network, anything goes. Communications can be diverted, copied, altered, replayed, rerouted, etc., etc., etc. We have no lingering familiarity and trust of open networks and though our data communications in open networks most often start with a point to point telephone link, there the similarity ends. Experts tell us that this new medium is notoriously insecure. Thus far, and for good reason, the business community is not shifting its trust of the traditional switched medium to open networks in the same way as it did during the widespread and rapid deployment of facsimile communications. And yet there is huge interest in promoting the development of what is currently widely described as electronic commerce.
[11] In truth, the whole notion of 'electronic' commerce is really a misnomer, because there is little, if anything, 'electronic' about it. What everyone should really be talking about is 'digital' commerce. Electronic or digital commerce is the transformation of paper-based transactions and processes into digital processes where the printed word on paper is replaced by the 1's and 0's of binary code. For the Internet to perform a role as an appropriate medium for commerce, there must be a way to make sure that the senders and recipients of 1's and 0's are known with some degree of reliability and that some mischievous spirit can't easily alter the sender's sequence of 1's and 0's on their way to the recipient.
[12] To understand the scope of the solution which is needed, it is necessary to understand the scope of commercial traffic that is desired to be carried over open networks in order to realize the promise of a fully implemented global information infrastructure. While retail commerce (wine or roses over Internet for example) is certainly part of the future of digital commerce, it is only a small part. There exists a whole spectrum of services (legal services, financial and accounting services, health care services8) which can be more efficiently provided with the assistance of open networks. There is also the very important matter of communications between the state and its citizens.
[13] Internet is the predominant and most important example in the world today of an open network and there are a good number of examples of businesses doing quite nicely with Internet commerce in the retail sector at the present time. The point has been made in the past that retail electronic commerce can, and to a certain degree will, flourish on open networks as they exist today without the need to bring copious amounts of technology to bear in order to provide high-grade messaging integrity, security and authentication services. But this argument applies only in so far as one considers the relatively narrow spectrum of commercial traffic represented by retail transactions and in particular the majority of credit card purchases. The following passage expresses the argument in favour of the sufficiency of existing systems:
[14] "The basis for this argument is that cyberspace, including the Internet as it stands today, can be a reliable channel of legal communication for people who use common sense. With sensible, low-cost measures, such as sending acknowledgments, following up with telephone calls, face to face meetings, or other alternative channels of communication, negotiating advance payments, using reliable network connections, paying attention to details, abiding by strict record keeping routines, and conducting business with a personal touch, the risks of electronic communication compare favorably with other forms of business communication such as courier, postal mail, telex, telegram, fax and telephone. The sending of an acknowledgment to an independently verified address is a particularly effective security measure. Although none of these measures provide military grade authentication of messages, few business messages need that much protection."9[15] It is certainly true that the foregoing measures can be effective in allowing Internet to serve the basic needs of retail commerce. But they beg the question whether the goal of resorting to the Internet is to increase efficiency in part by decreasing reliance on traditional means of communication. To the extent that Internet-based retail commerce dictates continued reliance on traditional out of band communications, then its ultimate utility can only be severely limited.
[16] In addition, this point of view does nothing to address the concerns raised by using open networks to serve the needs of the broader range of commercial traffic. There are formidable amounts of information recorded, stored and transmitted in the health care industry. The information is created and used by such diverse participants as medical professionals (doctors, nursing and para-medical staff), hospitals, clinics, insurance companies, federal, provincial, state and local agencies, and patients. The same is true in the financial and accounting industry and the legal profession. Such information flows make up a very large component of business communications and form the greater part of the broader spectrum of 'electronic commerce'. These types of information require a higher standard of care. In retail commerce, all that matters is that in point of fact most transactions get completed satisfactorily in spite of the occasional glitch. The broader spectrum of traffic has intrinsic value related more often than not to its confidential nature. Medical, financial and legal information must most often be reasonably protected from disclosure to the wrong parties. The present nature of Internet and other open networks fairly precludes their generalized use to carry such traffic. In fact, legal opinions have been given to the effect that Internet, absent special measures being taken to provide a reasonable assurance of confidentiality, integrity and authentication, is not an appropriate medium for transmitting privileged information.10
[17] In order to permit Internet, and the eventual information infrastructure to carry such communications effectively, it is important to be able to identify the individual communicating over the open network without regard to the physical location from which he or she communicates and without regard to the device which is used (personal computer (PC), personal digital assistant (PDA), network computer (NC), television set-top box, telephone or other information 'appliance'). In addition, it is important to know with some certainty that information sent over the open network will only be readable by the intended recipient, similarly without regard to the individual's location or the means of communication used.
[18] Simply securing the Internet data network to make it work more like the telephone network is not sufficient to accomplish the type of messaging integrity which the eventual information infrastructure demands. A point-to-point, line-switched communications network like the existing phone system succeeds in supplying a degree of confidentiality and a degree of authentication (restricted to the registered owner of the telephone line) but does little or nothing to identify the individual actually accessing the service without regard to his or her location.
[19] The technology required to permit the kind of security and authentication which is needed is already in existence, in the form of digital signature technology, but has yet to be deployed in a meaningful way. The advent of a useful global information infrastructure demands the establishment of a broadly-based, ubiquitous, inter-operable, open-standard, public key infrastructure. The objective of rolling out this technology is not to provide military-grade, bullet-proof confidentiality for e-mail communications, merely to provide the functional equivalent of the traditional means of communication to which commercial-grade information is routinely entrusted at the present time.
[20] Establishing local, national and global public key infrastructures
[21] The purpose of this article is to explore the legal and economic principles underlying the establishment of a broadly-based public key infrastructure. As such, it is not the role of this article enter upon an explanation of the principles underlying public key cryptography, digital signatures and public key infrastructures generally and the way in which this technology relates to the legal requirement for certainty in the formation and proof of contracts. Other authors have covered this ground very ably, both as regards the principles at play in the common law jurisdictions of the United States and Canada 11 and those which apply in civil law terms in the province of Quebec.12The authors therefore refer the reader to the appropriate articles for an in-depth discussion of the way in which digital signatures and public key infrastructures are capable of contributing the certainty required by principles of contract law as well as satisfying statutory signature requirements generally.
[22] In order for digital signatures to play a meaningful role in providing the underpinning for shifting our paper-based systems to an electronic paradigm, persons who will wish to use digital signatures must have access to a service or services which will allow them to manage their public and private13keys. While it is possible to use public key cryptography in the absence of a public key management service, the user will find to be much too burdensome the task of reliably distributing the public key or otherwise making it available for use by third parties, keeping track of the persons to whom the key was given so that they can be advised when the key requires replacement and eventually actually advising those persons when the key has become unreliable for any reason (all the while worrying that some third parties will not be informed in a sufficiently timely fashion). Resorting to commercial public key management services has the power to take the immense promise of public key cryptography and make it an every day reality.
[23] Not only must this service exist but it must be available to the broadest possible population of persons susceptible of wanting to transact in open networks. Public key infrastructures must therefore be ubiquitous if they are to be truly useful.
[24] In order to be ubiquitous, public key infrastructures must be very accessible in the sense of being easy, efficient and economical to use and they must comply closely with the needs and requirements of the key owner. These are two of the most essential criteria for fostering the necessary ubiquity. Because the goal of implementing a global information infrastructure is, at first, to permit most paper-based information flows to be shifted to an electronic medium, it is essential that the infrastructure accommodate all sectors of society. When one considers how very broad the coverage of public key management services must be, it becomes clear that a single service provider or even a single hierarchy of public key management service providers is unlikely to be in a position to accommodate and to service all those who will wish to participate. One must therefore envisage a future where there will be a proliferation of entities offering key management services to the public.
[25] The proliferation of key management services depends upon the existence of a market for key management services. In order for the market to exist there must be a commercial means of offering the service. One of the key ingredients which determines the spread of commerce is the perceived expectation of profit and the perceived degree of risk associated with earning the profit. The eternal twin principles of risk and reward. Because no human endeavour is ever devoid of risk, some degree of risk is inevitable. From that point on, all that a business can seek to do is to manage its business risk. Public key management services cannot escape the phenomenon of business risk any more than any other business can and anyone venturing into the public key management business must therefore have a risk management strategy.
[26] Basic principles of risk management
[27] What are the principal tools for the management of business risk? The prudent business must deal with risk by first identifying the risks it runs, avoiding those risks which may reasonably be avoided, shielding itself from the risks it cannot avoid principally by declining liability through contract or benefitting from so-called legislative safe-harbour provisions, and finally accepting those risks which it can neither avoid nor deter by insuring, hedging, financing or otherwise providing for the impact of the risk on its business. To the extent that a given endeavour does not lend itself to an efficient risk management model, the likelihood of turning it into a lucrative business is proportionately impaired.
[28] In order to ensure the proliferation of key management services, it is essential to provide an efficient risk management model for key management services which is susceptible of being used as a basis for business. Identification of the risks is the first step to be taken in attempting to build an economic model for a commercial public key management service. In order to identify the risks inherent in the management of public keys it is essential to understand the environment in which the activity takes place.
[29] Public key management protocols
[30] Public key infrastructures and the management of public keys they are destined to provide are intensely computational environments in the sense that the public key infrastructure must form an intimate part of the open data communication network. Transaction speeds on the part of the public key management service and the level of service it must provide on demand must match the pace, volume and speed of the data travelling on the network. The data flows are largely intelligible only to computers and can only be managed adequately in an information processing environment. As with most communications systems, the management of public keys relies heavily on generally accepted standards and protocols which determine the structure of the data flows required to be exchanged.
[31] Without much loss in generality, the scope of current approaches to public key infrastructures can be covered by reference to the ISO x.509 v2-3 certificate and key management standards,14Phillip Zimmermann's Pretty Good Privacy (PGP)system,15and Rivest's and Lampson's Simple Distributed Security Infrastructure (SDSI).16
[32] Pretty Good Privacy
[33] Conceptually, Pretty Good Privacy17(hereafter often referred to simply as "PGP") is one of the easiest to understand. An end user generates a public key and associates it with a reasonably unique identifier, usually a name/e-mail pair of the form John Doe, but potentially any other text string. Users can digitally sign keys, both their own and other users' public keys, and annotate the degree to which they trust that the identity of the key owner is correctly described by the key's identifier. Introductions are handled by users exchanging these signed key certificates. If Alice knows Bob, and Bob knows Carol, Bob can introduce Carol to Alice by sending Alice a digitally signed note attesting to Carol's identity. In the future, Alice can accept introductions from Carol regarding third parties, but the degree of reliance she puts on Carol's trustworthiness is quite independent of her relationship with Bob.
[34] Arguably, key compromise is the weakest link in the PGP public key infrastructure. In the event of a key compromise, users can create a key compromise certificate requesting that the particular public key no longer be used, but it is the end user who is responsible for disseminating the information to all possible end users a potentially daunting task. Furthermore, there is no notion of forgotten or misremembered passphrases, since a key compromise certificate must be signed by the compromised key. In this instance, users are advised to inform others of the key compromise as best they can. Since the use of PGP in the first place implies that standard communication channels are considered inadequate, this scenario leaves users with quite a dilemma.
[35] ISO x.509 public key management protocols
[36] A contrast to the laissez-faire public key management scheme adopted in PGP is the ISO x.509 standard,18currently being popularized in one of its many guises by the use of the Secure Socket Layer (SSL) protocol.19This set of standards provides a much more detailed and structured public key management model. Before we venture too far into this overview, however, it must be emphasized that there are at least three specific flavours of the x.509 protocols.
[37] Version 1 has been superseded by version 2, which remains the most popular version in implementations today. Version 3 was only recently standardized in June of 1996, and it is the proposed basis of the Internet Engineering Task Force s (IETF) Public Key Infrastructure using x.509 (PKIX).20Although most software and infrastructure suppliers have announced planned eventual support for version 3, version 2 is present in more than one very important implementation.21
[38] The x.509 protocol was originally designed as part of the x.500 world-wide telecommunications directory service, a service which subsequently failed to materialize in an important way. Accordingly, by reason of that heritage, the first two early versions of the x.509 protocols incorporated, and placed heavy reliance on, the concept of a distinguished name to identify its participants. Under the scheme of distinguished names, each certification authority and each end user would be identifiable by a name guaranteed to be globally unique by name registration authority(ies), an entity or group of entities that are possibly distinct from the certification authority(ies).
[39] The propensity towards a hierarchical structure of the x.509 protocol embodied in its use of distinguished names was eventually recognized as being not sufficiently flexible for widespread use.22It is for this reason, among others, that version 3 of the protocol, as currently envisioned by the Internet Engineering Task Force, drops the requirement that entities be globally and uniquely identified . In fact, in current proposals put forward b y the x.509 public key infrastructure working group23, public key owners could be identified in almost any manner, including by reference to their E-mail address, by reference to nicknames to Uniform Resource Locators ("URL"'s) and Uniform Resource Identifiers ("URI"'s).
[40] The current proposals leave open the option for certification authorities to attest not only the identity of their subscriber, but also the nature of the subscriber's authority to act on behalf of others, arguably a very important feature for the development of electronic commerce.
[41] The Simple Distributed Security Infrastructure system
[42] The
Simple Distributed Security Infrastructure 24system
(hereafter often referred to simply as "SDSI"), like its contributing precursor
PolicyMaker,25takes
a potentially radical approach to its method of identification of the principals26in
a communication session. To quote from the specification:
[43] "Our system is key-centric : SDSI principles are public digital signature verification keys. These public keys are central; everything is based around them. The notion of an individual (e.g. person, corporation, process, or machine) is not required. Of course, such individuals will actually control the associated private keys, so that the public/private keys can be viewed as proxies for these individuals." 27[44] From a computational point of view, this statement is completely correct; a digital signature is the only completely objective attestation as to the identity of the message's originator. From a more social point of view, it offers a somewhat twisted view of reality, somewhat akin to a person being identified by the keys on their pocket key chain. On the more positive side, SDSI encourages a much more free-form description of individual entities than does either PGP or x.509. Information such as pictures, driver's licences, affiliations, and other pieces of information may be freely attached by a willing principal, yielding a much more realistic picture of what is commonly held to be an individual's identity .
[45] Another aspect of SDSI is that it brings back the concept of distinguished names in a slightly different guise. Instead of each key owner having a globally unique identifying name, users are allowed to pick any identifier at all. References to other key names are then relative to the end user. In some cases, this is highly intuitive: your co-worker's supervisor's lawyer could be referred to as John's Boss' Lawyer, even though that individual refers to himself by a completely different name. In other cases, the constructs become slightly more artificial: a major international airline would be known as ThePhoneBook's AirlineCompany if the public key was obtained via the telephone directory.
[46] In a local setting, this system could work reasonably well. When inter-operating with others, however, difficulties arise. Suppose you wish to communicate with an individual for the first time. To do so securely, you need their public key. But to get their public key, you need to query your Key Distribution Centre with a reference: Please send me Bob's key. But which Bob? Since all namespaces are relative, my Bob and your Bob may be completely different individuals. SDSI attempts to solve this problem by the use of distinguished roots that are global names. To quote from the specification:
[47] "Our proposal is egalitarian: each principal can make (signed) statements and requests on the same basis as any other principal. No hierarchical global infrastructure is required. Of course, in practice some principals would be more important than others, and SDSI allows for some principals to have special status as distinguished roots, allowing SDSI to accommodate global names. But that is for convenience rather than necessity."28[Emphasis added.][48] For someone in the position of designing and seeking to implement a risk management strategy, this statement should be taken very seriously: written directly into the protocol specification is the requirement that global inter-operability with this protocol requires the acceptance of the innate superiority of some organizations over others; superiority meaning that the binding of the global name to a public key be hard-wired into the protocol. Technically, this convenience may be unused, but only at the price of most of what makes an idealized PKI such an incredibly useful thing: global inter-operability, allowing reasonably secure communication between previously unrelated parties.
[49] The last manner in which SDSI differs from PGP and x.509 is that it has been designed specifically from the ground up as an online protocol. Although SDSI certificates do have validity dates like every those implemented in other protocols, it is assumed that a certificate can always be checked for validity online, at the moment of need. Fortunately, there is no impediment to storing and using certificates off- line; the end choice on how to verify the validity of a certificate is left where it should be with the end user.
[50] Common denominators: certificate chains and certification practice statements
[51] Although these standards/protocols differ materially in semantics, coding, and usage, for the purposes of this paper they share some common features to the extent that implementations of them are generally thought to give rise to the use of certification authorities, certificate chains and certification practice statements.
[52] Certificate chains
[53] For our purposes, a certification authority (sometimes simply referred to in the literature as a "CA") is an entity that digitally signs a public key certificate which it is intended another party (the "third party" or "relying party") will rely upon. For example, if you signed a copy of your brother's public key together with a statement that this public key belongs to my brother, and then distributed this digital certificate for others to use, you would be acting as a certification authority for your brother. A certification authority is potentially any individual, entity, or organization that is prepared to act in this manner.
[54] A certificate chain in the context of the public key infrastructure implemented on the basis of the x.509 protocol has been described by Warwick Ford:
[55] "In a broad public key infrastructure, there are many CAs which certify the public keys of different sectors of the community. When a system needs to use a remote user's public key, it obtains this public key from a certificate which it validates by checking the CA's digital signature on that certificate. However, a certificate-using system cannot reliably know a priori the public keys of all CA's. Therefore, to obtain the public key of a CA, a certificate using system may need to obtain and validate another certificate -- a certificate for the CA's public key issued by another CA. This generalizes to the situation where a certificate-using system requires a certification chain. The chain comprises a certificate for the remote subject's public key signed by a CA, plus a series of certificates in which one CA certifies the public key of the next CA in the chain. The chain terminates with a CA whose key is already reliably known (through some independent means) by the certificate-using system."29[56] For a practical example of how a certification chain is presently contemplated in operation, the reader should refer to the Verisign Inc. Certification Practice Statement which describes at section 8 how the certificate chain pertains to the verification of a digital signature:
[57] "Such verification shall be undertaken in a manner consistent with this CPS, as follows:[59] The PGP system uses certification authorities and certificate chains as well, in the slightly modified guises of introducers and the web of trust. An introducer is someone whom you trust to introduce other people to you if they have signed a certificate stating that public key X belongs to Alice, then you can trust that statement. The web of trust is often misunderstood: if you have signed Alice's key, and Alice has signed Bob's, and Bob has signed Carol's, you do not have to put any faith at all in Carol's identity. The web of signatures connecting you Carol does tell you that at the very least, that Carol's key is most likely valid and has not been compromised.31 Unless you decide to trust Bob to do introductions, however, you know nothing about Carol's actual identity.[58] Establishing a certificate chain for the digital signature - A digital signature shall be verified with regard to a successful confirmation of certificate chain."30
[60] Also note that an important component of the above scenarios is the context in which the chain occurs. In an intra-organizational model, where the public key infrastructure is contained within the same enterprise,32a certification chain may be quite practical and efficient for a sales representative to contact the marketing department. The risks and how they are dealt with are potentially quite different under an inter-organizational model, that is, when two completely unrelated parties from unrelated enterprises33wish to communicate. For the purposes of this paper we will assume that the parties are unrelated, which is the more problematic case. This would include the case where the unrelated parties actually have embedded certification chains; an example would be in trying to find a sales representative for a company. In principle, one need only find the public key of that company, and from then on one can comfortably descend the company's internal certification chain to the key of the representative since legally you are dealing with the company and not necessarily the individual.
[61] Certification practice statements
[62] Certification policy statements34or certification practice statements are intended to permit the certification authority to explain its practices to potential users of its certificates including its subscribers and third parties:
[63] "A certification practice statement may take the form of a declaration by the certification authority of the details of its trustworthy system and the practices it employs in its operation and in support of issuance of a certificate, or it may be a statute or regulation applicable to the certification authority and covering similar subject matter. It may also be part of the contract between the certification authority and the subscriber. A certification practice statement may also be comprised of multiple documents, a combination of public law, private contract, and or declaration. A certification practice statement is useful in helping subscribers and relying parties distinguish which certification authorities provide more reliable representations in the certificates they issue."35[64] Certification policies or certification practice statements are therefore guidelines and rules of conduct which express in legal terms the extent to which any given public key certificate is intended to be relied upon. These practice statements or policies affect how a certification authority , its subscribers and relying parties36 manage their risk because they influence the interpretation to be given to any given digital signature.
[65] Identifying certain business risks under currently proposed key management protocols
[66] There are a great number of risks which are, or which will be, inherent in the business of public key management services.37In this regard, the public key management business will not differ to a material extent from all other businesses. Just like any other business, the public key manager must identify the risks it will run, avoid the risks which it can reasonably avoid, shield itself from the risks it cannot avoid through the use of contracts or safe-harbour legislation and finally hedge against, insure or finance the anticipated impact on its business of the remaining risks.
[67] It is not our intention, nor would it be realistic, to attempt, in the context of this article, to catalogue every conceivable risk to which a public key management service would be exposed in the ordinary course of its business. Our intention is merely to identify certain major aspects either of the existing public key management protocols or of the ways in which they are presently proposed to be implemented which we feel contribute unnecessarily to the risk that a public key management business will eventually face.
[68] Because the risks are so numerous, varied and potentially material, it is essential to ensure that the economic model which is ultimately adopted for the public key management service is as efficient as possible in managing risk. The currently proposed public management protocols feature architectural elements which in our view tend to militate against an efficient risk management model and hence they do not, in their present conception, provide economically efficient platforms for the establishment of a ubiquitous public key infrastructure. Those elements are the following:
[74] We submit that these failures and negative features can be all be easily and simply addressed without any great difficulty and that the alternatives we propose will result in a technical and legal platform for public key management which will be far more responsive to the needs of all the participants and far more efficient in allowing each of the parties who must participate in a public key infrastructure to manage the risks to which they will be exposed in the normal course of events.
[75] Architectural elements of an efficient global public key infrastructure platform
[76] The currently proposed public key infrastructure protocols are primarily concerned with the establishment of a shared technical means of implementing the infrastructure. While there may be many different and equally good means of managing a public key infrastructure from a purely technical point of view, it is naturally to be expected that some alternatives and approaches will be superior to others in the way in which they perform from an economic and risk management point of view. In their present form, the public key infrastructure protocols ignore, to a certain extent, the realities of our existing traditional communications paradigms. As such, the existing protocols, and the legislation which has grown up around them, do not allocate risk among the participants in ways to which we have grown accustomed.38
[77] The goal in implementing any public key infrastructure ought to be merely to shift the current paper-based paradigm39in which our information management currently functions and not to replace it. The digital signature is potentially a very powerful communications facilitation tool. In some important respects digitally signed data is vastly superior to the signed paper document upon which we now generally rely. It is therefore tempting to want to exploit the implicit power of this new technology right from the outset so as to leverage human communications onto an entirely new plane. Consider for instance the proposal to deploy digital signature technology as part of a new professional specialization for lawyers involving CyberNotaries:
[78] "This [resorting to a CyberNotary] will be particularly the case where the user is purporting to execute the transaction on behalf of another party (i.e. corporate power of attorney) or wishes to have his transaction be enforceable in a civil law jurisdiction,40where there are rigorous authentication requirements. In either instance, the intervention of an [sic] CyberNotary is irreplaceable. Neither the mere application of a digital signature, nor a legal undertaking of a U.S. lawyer or notary satisfies authentication requirements for these types of transactions. The CyberNotary will combine the functions of digital signature verification, legal practice, and notarial intervention to provide high level international authentication in a measure far exceeding current practice."41[clarifications added][79] Such a fundamental change in the way in which humans relate to each other would probably amount to replacing rather than shifting our existing paradigm.
[80] Before we learned to run we had to learn to crawl and then to walk. The reality we face is that the simple shifting of our paper paradigm over to a digital one, though it may be a modest transformation in the quality and substance of our communications habits, requires a considerable adjustment in our legal and social institutions which has the potential to make the transition a relatively delicate and slow moving affair.42 The best means to encourage a smooth and relatively rapid transition is to mirror as closely as possible in the new medium the customs, mechanisms and traditions we have come to accept and rely upon in our paper-based transactions. To the extent that we can simply transpose the things we do now into the new information scheme, without appreciably changing our exposure to the risk of liability, there will be a more ready understanding of the new medium and fewer impediments to its development and widespread adoption.
[81] Geodesic domes versus pyramids
[82] One of the features of the currently proposed public key management protocols which we mentioned above is a relatively strong tendency towards the organization of public key management services into hierarchies, and specifically into pyramidal hierarchies. Hierarchies have many practical applications. They are neat, they are tidy and they are highly functional. Hierarchies can serve a very useful purpose as a pattern for organization, particularly where a centrally controlled industrial or computational process is desired.
[83] It has been observed that the telephone industry is highly prone to the use of the pyramidal hierarchy in everything from the design of telecom systems to management structures.43In many ways the currently proposed ITU x.509 certificate standard44is a child of the telecoms and other large public companies, and it is no coincidence that public key infrastructure proposals based on this standard tend to be more obviously hierarchical than others.45
[84] Pyramidal hierarchies are not very easy to impose on human beings in their daily intercourse. Human beings, and many types of businesses and organizations, naturally seem to prefer looser, freer relationships than pyramidal hierarchies allow. The larger the population one targets, the less likely it is that a pyramidal hierarchy can work as an organizational model. A pyramidal hierarchy can certainly work well enough on a limited scale for a limited purpose (a business enterprise certainly, a social club, etc.) and it can even scale up reasonably well to accommodate some relatively large populations (a large multi-national corporation, an army, even a world-wide religious order), but inevitably the pyramidal hierarchy as an organizational model begins to fail when it is attempted to apply it for a relatively wide variety of purposes or to truly large populations. The pyramid requires a high degree of consensus in order to work well and the development and maintenance of that consensus becomes virtually unworkable in very large systems. In large systems such as an open global communications infrastructure a different organizational model is required.
[85] Internet works so well because, in the end,46it does not follow a hierarchical model. Internet, which is the pre-cursor of the eventual global information infrastructure, may be more properly described as a geodesic organizational model. The geodesic model derives its strength from a cooperative structure in which any individual element is relatively weak and ineffectual but where the interconnections lend incredible resilience and cohesiveness. The rupture of one small link, or even of many small links do not destroy the system. The Internet owes its explosive growth, in part at the very least, to its geodesic organizational structure. This structure allows free form expansion and almost unlimited scalableness.
[86] It therefore seems to make sense, at least on an intuitive level, to eschew a pyramidal hierarchical organizational model when designing a public key management model for the global information infrastructure. If we think of a hierarchical certification infrastructure implemented as an inverted pyramid, it becomes clear that the risk associated with a compromised key is amplified in the same way that we use a cone to amplify sound in a loudspeaker. If a key compromise occurs towards the apex of the inverted pyramid, the whole ascending certification chain suffers from the compromise and the potential problems and the risk associated with that compromise are naturally amplified as well. This weakness inherent in the x.509 protocol has already been identified:47
[87] "The more levels there are in a certification tree, the more certificates Alice needs to check to ensure that Bob's certificate remains valid. Suppose that Bob's digital signature is supported by a certificate issued by CA1, which has a public key certified by CA2, in turn certified by CA3, which in turn is certified by a state government. If the state government issues a notice of revocation for the certificate of CA3 because, for example, someone has broken its private key, all certificates descending from CA3 are now suspect."48[88] In addition to exacerbating the risk posed by a key compromise occurring in the certification chain, certificate or certification chains pose interesting problems for the interpretation of certification practice statements and certificate policies. It is not enough to follow the logical certification chain when validating a digital signature: the semantic interpretation associated with each certificate must, when combined, yield a desirable result. While current computers excel at doing simple comparisons and checks, more complex and varied terms of signature resulting from the concatenation of a number of varied certificate policies and certification practice statements may well defy all attempts to make sense of the result.
[89] There is nothing however which legally compels the adoption of the pyramidal hierarchical model.49
[90] The implementation of a geodesic organization model for a global public key infrastructure is something which can be done.
[91] In order to minimize the pyramidal hierarchy of the eventual multitude of public key management services in a public key infrastructure, it is necessary to dissociate the flow of trust from the flow of information. The presently proposed public key management protocols closely associate the flow trust with the flow of information. Thus trust flows in a chemical or biological way by being bonded with the information through the mechanism of the digital signature itself. Whether one resorts to a decentralized certification hierarchy with multiple levels of certification authorities cross-certifying each other or to a more centralized certification hierarchy with perhaps two levels of certification authorities at most,50 the way in which the current protocols are proposed to be implemented still provide for the certification authority's public key to be signed by the certification authority above it in a hierarchy.
[92] The principal mechanism which is adopted by the existing protocols as a trust vector is therefore the certificate chain: a chain of public key certificates which creates a link between the third party and the subscriber's public key.
[93] Because a public key infrastructure is a computational environment, it is tempting to solve all problems computationally and logically. The whole raison d'être of the public key infrastructure is, in the end, to vector identity and trust. It is not surprising then that attempts are made to bond the issue of trust to the information which is conveyed about the identity of the subscriber. This leads to the logic of the certification path and certificate chains: Alice trusts Bob who trusts Carol who trusts Doug, and computationally this implies that Alice can trust Doug.
[94] In fact, this chemical, electrical, biological or computational treatment and 'vectoring' of trust in a public key infrastructure under the currently proposed public key management protocols injects a tremendous amount of complexity in the process while at the same time accomplishing very little in the way of actually providing an appreciable level of true security. For while the technique of the digital signature gives rise to a high degree of certainty that signed data was created with a particular private key, in the end that assurance we experience must always rest on the trust associated with the binding between the root key or root keys and the entity which is perceived as the font of trust. By definition this can never be a hermetically sealed self-sufficient system. At some point in the process, the objective security ends and risk and uncertainty inevitably re-assert themselves. The final reality to which we must reconcile ourselves in the real world is that trust is not like water or electricity, it cannot be reliably vectored with plumbing, wires or lines of code:
[95] "Yet I would put forward what some may view as a heretical statement: security is not a simple technological issue. Indeed "doing business securely on the information highway" is not a simple matter of developing the right technologies to "lock up" information sent electronically to protect it against theft or alteration, nor is it a simple matter of developing authentication techniques that allow us to determine with extreme accuracy who was the actual originator or creator of a given message. Rather, the "security" which business people seek when they begin doing business electronically requires the creation of an entire infrastructure - legal, social, economic, political; an infrastructure based on practice -- which recognizes, validates and supports electronic commerce." 51
[96] To
the extent that certification hierarchies do not suffice in and of themselves
in providing all of the assurances we may need, how can we create a reasonably
trustworthy public key infrastructure? The answer lies in a large number
of variables which together justify the trust we place in institutions
in our society. Parallels exist in other industries. We trust our banks
because we know that they are subject to mandatory controls on their operations
designed to ensure that their operations are carried on with a degree of
financial propriety. The same is true of other sectors of the financial
services industry including insurance companies, securities dealers and
trust companies. Some of the assurances are based on legislation and government
regulation, others arise from self-regulatory initiatives or voluntary
compliance with industry standards. To a large degree our faith in our
institutions arises from the statistical incidence of failures and losses
and the degree to which abuses are dealt with fairly. There is no reason
why the public key management business should obey different rules. Should
Verisign Inc.'s public key certificates be any less trusted because Verisign
Inc.'s root key is self-certified? Would its certificates be any more trustworthy
if its certificates were signed by one or more senior certification authorities?
[97] It can be argued, as we do, that having the Verisign Inc. key signed by a senior certification authority or many senior certification authorities, however trustworthy they may be, actually impairs the trustworthiness of Verisign Inc.'s certificates since it multiplies the possible consequences of a key compromise higher in the hierarchy. In addition, there is the substantial problem of making sense of a variety of certification practice statements and policies which eventually aggregate with those of each certification authority upstream or downstream in the certification path.
[98] If all that existed was a mandatory standard of quality for public key management services to which certification authorities adhered in circumstances where the compliance by the public key management service with the standard was reasonably verifiable by out-of-band means, no requirement would arise for cross-certification, certification hierarchies, certification paths or certificate chains.
[99] Once the public key infrastructure is freed from these requirements, the question of how the third party goes about obtaining public key certificates and certificate revocation lists or certificate status certificates and assurances becomes much simpler and any number of technical means of providing the service can be envisaged. In addition, the only certification practice statements or policies with which the certificate users will have to come to terms are those of the certification authority actually issuing the subscriber's public key certificate52 which avoids a large amount of potential confusion.
[100] By way of very brief example which supports such an approach from a technical point of view, one need only turn toward a common, everyday telephone directory. If an example with slightly more technological luster is desired, one can look at one of the many Internet search engines on the World Wide Web today such as Lycos,53 InfoSeek,54 and Alta-Vista.55 On the less technological side, a telephone book can be viewed as a database of individuals, organizations, companies, and government departments that can be indexed by some sort of name and or type of service or product. Internet search engines provide the same task on a vast new level: a user requests documents indexed by certain key words or phrases - these are the mnemonics by which they and hopefully others index the type of information they are looking for in their minds. The search engine then sorts and retrieves large, more detailed descriptions of documents that can be indexed by the selected key words. The end user can the peruse these more detailed descriptions to find the one or two which most closely match what he/she intended in the first place. If sufficient level of detail and description is found, and/or if the description matches what was intended closely enough, the user may choose to hyperlink to referenced webpage for further study and communication. The actual webpage itself is found by the identity of a URL - a sequence of characters largely incomprehensible to most people, but nonetheless sufficient to identify uniquely the intended Internet destination.
[101] It becomes clear, when one analyses the very basic nature of digital communications and the very nature of digital signatures, that no system susceptible of being deployed will succeed in eradicating all possible means of compromising the integrity of messages conveyed by the infrastructure. In all the history of mankind, there is not a single instance of such a communications medium. Every supposedly secure system has failed to achieve a perfect record of integrity and trustworthiness. For the more valuable the secrets, the more opaque the security, and the greater the resources deployed to compromise them. All we can hope to achieve in the end is to manage the risk. We will have succeeded if we craft a medium which provides an acceptable level of security at an acceptable cost. The remaining risk will by definition be acceptable if it gives rise to sufficiently desirable rewards.
[102] We submit that an approach to the certification of public keys such as the one we suggest is sufficiently flexible to permit a global inter-operable public key infrastructure to be deployed which will provide an appropriate degree of assurance which will be equal to or which will exceed that which we currently enjoy with our traditional means of communication and which can serve as an appropriate and economically efficient foundation for the deployment a true information infrastructure.
[103] Jack of all trades, master of none
[104] Unfortunately, there is a perception that public key infrastructures not only can but should centralize virtually all the roles required to be played by a public key infrastructure in the hands of the certification authority. Even the use of the word 'authority' to describe the key management service testifies to the centralizing and authoritarian nature of the protocols.
[105] Thus, it sometimes assumed56that the certification authority will attest not only to the binding of the subscriber's identity to a public key pair but also to the aspects of the subscriber's identity which determine the subscriber's quality, accreditations and authority to act for and to legally bind others.
[106] Identification is the central role of the certification authority and as such it is natural when one goes about the task of designing a protocol for what in the end is intended to describe a computational process, to attempt to deal with all of the identification issues in a single central step. While this is a very efficient way of describing a computational system or an industrial process designed to link two entities in space and time (i.e. the person and his public key), it neglects to consider that on a human and organizational level, the question of identity is a very subtle notion whose nuances go to the very core of human social and economic interaction. So much so that we submit that it is ultimately completely unrealistic to expect to offer successfully a certification service to the public which fails to deal in an appropriate way with the many issues which arise in attempting to come to grips with the seemingly mundane question of identification.
[107] Let us first consider that the issue of the identity of any person or other entity is comprised of facts which are true in relation to the person or entity.57 The sum of those facts is what makes up the identity.
[108] Examined more closely, it is easy to determine that those facts can be broadly classified into two main categories: those facts in respect of which the essential relationship between the person and the fact is relatively static and those facts where the essential relationship is relatively dynamic. The passage of time makes dynamic facts into static facts. The present and the future are dynamic while the past is static. This principle rests on a belief that time is an infinite continuum. Some may differ, but for most of us however, this is a relatively safe statement to make. In the context of the example which follows, which is based on the life of Benjamin Franklin, it is only possible to distinguish the static facts from the dynamic facts if one places one's self at a given point during Benjamin Franklin's life.
[109] Consider
for example the following table of facts relating to Benjamin Franklin58which
make up the essential ingredients of his identity:
|
|
|
|
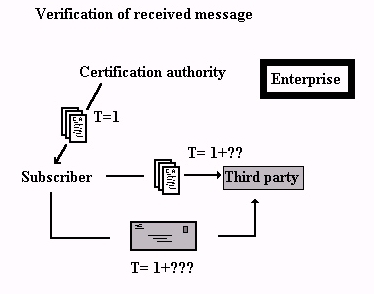
|
|
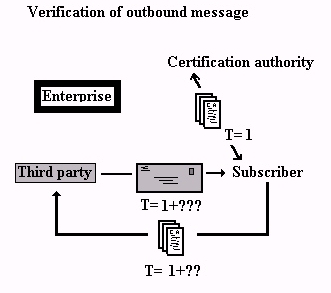
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
[110] We say that a fact is relatively static or dynamic in the sense that it depends very much on the current circumstances and point of view. A fact tends to be more static to the extent that its relationship to the person is not susceptible of changing. To the extent that the relationship between the fact and the person is constantly in a state of flux, the fact tends to be more dynamic. When and where we were born is a good example of a static fact about us. Who our employer is from time to time or where we live may be good examples of dynamic facts about us.
[111] Consider the foregoing hypotheses in the context of the life of Benjamin Franklin. Benjamin Franklin was a very dynamic individual, to say the least, and he led a very dynamic life. In 1763, he was a resident of America. At the time, the question of his residence could only have been said to be a very dynamic fact, considering that in 1762 and 1764 the same question would have revealed him to be a resident of England. The second most static fact of his life was that he died in 1790 in Philadelphia. He ceased to be dynamic in every sense as and from that time and all facets of his life became history, hence static facts, including his brief residence in America in 1763.
[112] It should be finally noted that the determination of whether a fact is static or dynamic is at least in part a subjective exercise and the results therefore tend to vary depending on the circumstances and point of view of the observer. Thus, for most of us and for most of our business and personal needs, it is safe to assume that a person's sex changes infrequently enough to consider it to be a static property. The Official Olympic Organizing Committee may not however share that opinion and accordingly may wish to scrutinize Olympic athletes more closely for gender changes.
[113] The task of identifying any person is fraught with no small degree of difficulty. There is, and always will be, the risk that we make mistakes in relating the facts to the person we are attempting to identify. To the extent that we restrict the identification of the person to static facts, the task, though still delicate in many respects, is made much easier and far more certain. It is impossible for a person to change the date and place of her birth or the identity of his parents. It is relatively unlikely that the person's sex will change. The person's appearance is another matter (disguises being the all-time favourite human trick in the art of deception) and from there on, the relativity of information about the person's current circumstances becomes less and less static and more and more dynamic.
[114] The most dynamic of the facts relating to any person is the quality in which they may act from time to time. By quality, we mean the bundle of facts which denote the authority of the person. In other words, what authority does the person exercise? Is the person a master mechanic, a brain surgeon, ballerina, airline pilot, president of the United States, secretary-general of the United Nations? All of these facts attest to the relationship which any person has to other persons in a society and the person's quality is defined by the continued existence of that relationship. Relationships are essentially dynamic however and are subject to change at any moment. The file room clerk gets promoted to purchasing agent, attends night school, graduates, is promoted to regional manager, performs brilliantly and becomes vice-president operations, then chief financial officer, participates in insider trading, and is forced to retire in disgrace, a wealthy woman.
[115] The public key management service59is on complicated but relatively stable ground, in as much as it restricts its practice to binding persons to their public keys in reliance on static information.60The moment the public key management service takes upon itself the role of attesting to the quality or authorization of persons in relation to their public keys, the task becomes far more complicated, far more delicate, and the risk attendant to the task rises immeasurably.
[116] Let us take a simple example: Benjamin Franklin as Deputy Postmaster General of the colonies. Benjamin Franklin exercises that function for a relatively long period of time, from 1753 to 1774, largely in England, though not as we have seen in 1763. The best person to manage the continued authority of Mr. Franklin would be his immediate superior. If Benjamin turned out to be less than trustworthy (suppose it was discovered he was fomenting a revolution in the colonies), the trust and authority he enjoyed would naturally have to be curtailed. His employer, the King of England, is the most suitable person to manage all the features of that relationship since it is the employer who bears the risk of disloyalty, it is the employer who best understands the risks and what is financially at stake, and it is the employer who decides whether or not to bestow his trust on the employee.
[117] If one interposes a third party, however earnest and trusted that third party may be, between the employer and the employee, as custodian of the authority bestowed upon the employee by the employer, that third party is called upon to manage something she has no control over, in a situation where she doesn't fully grasp the intricacies of the relationship and where she has no immediate, controllable and reliable access to information ('have you noticed that since Ben got back from Philadelphia in 1764, he doesn't laugh at those great colonist jokes so much any more?'). Nevertheless, it is unlikely that the intensity of the duty of care she owes to her subscribers or to the public will be in any way reduced or attenuated in consideration of the remoteness of her position.
[118] In the context of a modern-day public key management service, it seems reasonably clear that the task of binding the static identity of a person to a particular public key pair is likely to be a very manageable task for which there are existing parallels (social security cards, passports, credit cards, drivers' licenses for example) on which to base both the service and the process. The task of binding the dynamic authority, the credentials of a person to a public key pair is quite another matter and for which it is far more difficult to think of existing parallels. Most authorization schemes are self administered by the person bestowing the authority and bearing the risk:
[124] Suggesting that certification authorities attest to the accreditation of subscribers in our opinion represents much more a complete paradigm change than a relatively modest paradigm shift.
[125] While there does not exist any legal requirement which at this time would require a public key management service to attest to the authority or capacity of a subscriber,63 since the distinction between attesting to a subscriber's authority and attesting to his/her identity is not necessarily a clear issue at all, this is precisely what may inadvertently occur.
[126] There is no reason why the existing public key infrastructure protocols cannot be adapted to the implementation of an architecture where the responsibility for attesting to the authorization bestowed upon a subscriber lies where it belongs, with the accrediting or authorizing entity. For instance there is nothing which presently precludes a design where enterprises are given the software and hardware to manage their employees' credentials themselves. The public key management service attests the identity of both the enterprise and its employees while the enterprise alone attests to the authority of a particular person whose identity is attested to by the public key management service. The enterprise would issue a type of certificate which we have chosen to call a credential certificate.
[127] The same communications protocols needed to permit the dissemination of public key certificates which we describe briefly above when suggesting a flatter more geodesic architectural model for a global, inter-operable public key certification infrastructure can be relied upon to implement a system of enterprise credential servers.
[128] The tail of the Pushmepullyou
[129] We apologize for the fairly whimsical section heading and as well to Hugh Lofting for associating his very entertaining literary work64 with what is, by comparison, a tedious cocktail of law, computer science and cryptography, but Mr. Lofting's imaginary beast fairly well describes one of the unresolved choices facing anyone who proposes to venture out in the waters of commercial public key management services. The reader will recall the poor Pushmepullyou, a kind of two-front-ended Llama. It was never really possible to know whether the animal was being pushed or pulled.
[130] A choice must also be made in the realm of public key management services as to whether public key certificates are pushed by the certification authority65 out to those in need of them or rather pulled from the certification authority as they are needed.66
[131] "Push refers to procedures whereby the FCA [Federal Certification Authority] delivers certificates and CRLs [Certificate Revocation Lists] to specified users and entities. Pull refers to procedures where persons desiring certificates or certificate revocation status information either perform a directory look-up or submit a request to the FCA (or to an FCA designated directory / database entity) in order to obtain certificates and certificate information. Authentication and acknowledgement of both send and receive events will be important for both push and pull approaches."67[133] Of all the many activities that a certification authority takes upon itself, the issuance of public key certificates in some ways marks the beginning of the certification authority's exposure to legal risk. While a certification authority may get sued for failing to perform its duties to a subscriber or to a third party prior to the time when a public key certificate is issued69 most of the important concerns in relation to the risks inherent in the operations of a certification authority commence from the time that it issues its first certificate. In particular, the certification authority is exposed to the risk of liability at the suit of either its direct client (to whom we will refer throughout this discussion as the subscriber) or of the third parties who come to rely upon the public key certificates (to whom we will refer variously either as the third party or as the relying party) for the purpose of either encrypting outgoing messages or verifying digital signatures on incoming messages.[132] "The various methods for updating and promulgating CRLs [or public key certificates] offer opportunities and risks. One major decision concerns whether, as a default/baseline, to push or pull CRLs. To evaluate this issue properly, the costs of a push strategy (including telecommunications costs), legal requirements, risks and, of course, the overall level of assurances which the FCA desires must be meticulously considered."68 [clarifications added]
[134] There are a great number of legal issues which arise when one begins to consider the nature of the relationship between the certification authority, its subscriber and the relying parties and the nature of each party's exposure to the risk of liability.70 There is no shortage of issues to consider and unfortunately there is a dearth of authorities to resort to when attempting to come to grips with them. Our intention in this section is not to offer a broad solution for the management of all the perceived risks liable to arise in the context of these relationships. In fact the scope of our suggestion in this section is limited to the resolution of only one aspect of the key management puzzle, albeit an important one, that is whether the certificates issued by a certification authority ought primarily to be pushed or pulled from the public key management service.
[135] The principal risks of pushing public key certificates
[136] As we have indicated earlier in this risk paper,71 can never be eliminated but it can be managed. One of the best tools available for the management of business risk is the legally binding contract. In the realm of the relationships among the parties in a public key infrastructure, the establishment of a contract has been recognized as one of the key avenues for risk management. It is primarily through contract that it is proposed to manage the risks arising in the relationship between the certification authority and its subscriber.72 The particular mechanism relied upon is the entering into of a relatively simple form of contract which then incorporates by reference the certification practice statement put forward by the certification authority.73
[137] The question of how to manage the risk posed by the relationship of the certification authority to the relying party is by no means as certain. To fully understand why this is so, it is necessary to understand the way in which the relationships between the parties arise under the currently proposed public key management protocols and rules.
[138] There are two sets of circumstances which must be considered in turn since the relationship dynamics differ in each case: there is the case in which an encrypted message is about to be sent and the case in which a digitally signed message has been received. Let us consider the information flows in the following diagram:
[139] Verification
of an incoming message with a pushed certificate
[141] Encrypting an outgoing message with a pushed certificate
[142] The diagram above shows the following: similarly in this model, in the beginning (time or "T" being equal to 1), the certification authority issues a public key certificate to its subscriber. Some time later (we don't know exactly when, T=1+??) the subscriber provides the public key certificate to the third party. Some time later still (T=1+???) the third party uses the public key certificate to encrypt a message which he sends to the subscriber. The subscriber's employer (still "enterprise" in the diagram) is still not directly involved as a participant in this process, hence the Chinese wall still drawn around the enterprise.
[143] The communication model in both of the foregoing diagrams is a push model where the certification authority pushes the public key certificates first to the subscriber and then to a repository (most likely a Web site). The certificates are eventually most likely again pushed to the third party.
[144] This push scheme presents several important deficiencies. First and most importantly, if we look carefully at the diagrams and think about what is happening, we notice that the risk is always generated by the reliance which the third party places on the public key certificate.74 Nothing really terrible is in fact likely to happen until the third party either (i) wishes to send information he considers to be confidential and therefore wishes to encrypt it using the subscriber's public key, or (ii) wishes to rely on the authenticity and integrity of the message he receives from the subscriber and therefore seeks to verify the subscriber's digital signature.
[145] The certification authority bears a great deal of that risk since it is the certification authority on whom everyone relies to provide the vital information (the public key certificate) which serves to protect the parties. And yet the certification authority and the third party, arguably always two out of the three key participants, have no way of knowing each other, or even of knowing the specific time frame within which the third party's reliance will take place.
[146] As we have seen, because the dynamic nature of facts relied upon by the certification authority changes with time, one of the dynamic facts being the identity of the subscriber's public key, the longer the period of time which elapses between the issuance of the public key certificate (at T=1) and the reliance upon the certificate (at T= 1 + ???), the greater the potential risk. And yet, because the third party and the certification authority are strangers, they can't even resort to the most important risk management tool (a contract) to manage the risk to which they are exposed.
[147] The law relating to third parties
[148] One of the truly shifting and uncertain areas of law is the area which deals with the legal relationship between a third party and principal actors (the principal actors being the parties to a contract or the immediate persons involved in a situation where liability sounds in tort at common law or in delict in civil law).
[149] The legal principle of privity of contract, a concept which limits the liabilities and rights under a contract to the persons who are party to it, comes into play and generally prevents a third party from either claiming rights under a contract or from being bound by its provisions. This is a principle which is well understood and which applies both in common law and civil law jurisdictions and thus may be considered to be of global application. The principle is not without its grey areas however. There are special situations where the principle of privity of contract has been relaxed in favour of bringing third parties into the contractual relationship either for their benefit or to their detriment. In particular, the law of product liability has stretched notions of privity of contract and tort or delictual liability to allow manufacturers of defective products to be held liable and for consumers to sue them. Once again, this relatively elastic conception of the otherwise generally rigid law of privity of contract applies both in common law jurisdictions and in civil law jurisdictions and it is therefore a feature of the law which is a global phenomenon.
[150] There is a similar problem in the law of tort liability or delictual liability in that the victim of a tort generally has a recourse against the person who is the proximate cause of the damage. To the extent that a person is somewhat removed from the event giving rise to the liability (which is by definition the case of persons conceived of as third parties) the law begins to fail to consider them in the scheme of liability. Once again, as with privity of contract, the extent to which the law brings third parties within the ambit of the circle of liability in cases of tort at common law, or in cases of delict in civil law, is somewhat elastic.
[151] Unfortunately it is not true to say that the elasticity of the law regarding third parties is constant in all jurisdictions and therefore it is very difficult to come to a reliable conclusion in relation to the rights and obligations of third parties, particularly where they reside in different jurisdictions. In fact, even within a single country like the United States or Canada, the treatment of the subject can vary substantially from state to state and from province to province.75
[152] Consider the following analysis by Prof. Froomkin:
[153] As regards privity of contract and third parties:
[154] "Today, the picture is murkier. The Restatement First test, the intent to benefit and its variations, and the Restatement Second tests are all inadequate and indeed largely meaningless. Courts have relaxed the privity requirement in contract, as in tort, replacing it with tests such as
[157] As regards liability sounding in tort:[156] Nevertheless, courts remain reluctant to allow everyone [to] be a potential third-party plaintiff in contract actions."76[155] the balancing of various factors, among which are extent to which the transaction was intended to affect the [beneficiary] the foreseeability of harm to him, the degree of certainty that the [beneficiary] suffered injury, the closeness of the connection between the defendant's conduct and the injury, and the policy of preventing future harm.
[158] "States differ greatly on when a third party can obtain redress for negligent misrepresentations. Some require only that the third party's reliance be foreseeable; most follow the Restatement (Second) of Torts rule which is an uneasy, and sometimes unclear, compromise between the two views; a few require contract privity."77
[159] This
uncertainty as to the regime of legal liability which will be brought to
bear when problems arise (for problems always arise) is, to say the least,
not conducive to the development of a thriving market for public key management
services.
[160] One solution is the adoption of legislation designed to resolve the uncertainty. For instance, the Digital Signature Act adopted by the state of Utah expressly provides for the third party's right to rely on the public key certificate as well as the obligations of the certification authority to the third party:
[161] "Representations upon issuance[162] While other jurisdictions in the United States have either adopted or are proposing to adopt digital signature laws of their own,79 often patterned on the Utah Act, and while such legislation is contemplated elsewhere,80 there can be no assurance that such 'safe harbour' legislation will become ubiquitous in the near future. In fact, it is not unusual to find that there is a degree of skepticism about the need to adopt legislation which deals in such detail with the management of digital signatures.81By issuing a certificate, a licensed certification authority certifies to all who reasonably rely on the information contained in the certificate that:1. the information in the certificate and listed as confirmed by the certification authority is accurate;2. all information foreseeably material to the reliability of the certificate is stated or incorporated by reference within the certificate;3. the subscriber has accepted the certificate; and4. the licensed certification authority has complied with all applicable laws of this state governing issuance of the certificate."78
[163] In addition, the approach to the allocation of risk and liability adopted in the Utah legislation has been criticized as unduly favourable to the certification authority and as imposing an unfair burden on the subscriber.82 Such doubt and criticism undoubtedly play an important role in fostering legislative caution and circumspection among legislators. Accordingly, some states have adopted a more 'technology neutral' approach to the issue of the admissibility of electronic records83 and to that extent it is somewhat unlikely that detailed digital signature legislation will be adopted in those jurisdictions.
[164] The case in favour of pulled public key certificates
[165] While it is not possible to achieve the same result in terms of predictability and uniformity of outcome as is possible through the adoption of specialized digital signature legislation, it is possible to modify the proposed technological model of the public key management service slightly in order to achieve more efficient data flows which can permit and even promote more efficient risk management.
[166] We have seen that the currently proposed public key management protocols implicitly contemplate a push method for the dissemination of certificates. We have also seen that this method fails to a certain extent in that it leaves the relying party in a tenuous legal position relative to the certification authority and also results of necessity in relatively long shelf lives for public key certificates84 which exacerbates the risk further. The less than ideal nature of this scheme has not escaped attention among information security professionals.85
[167] But what if public key certificates had extraordinarily short life spans? At the very least, this would tend to reduce significantly the direct risks attributable to stale information:
[168] "The risks that the reality represented by the certificate is out of date can be controlled, but not eliminated, by ensuring that certificates are dated when issued, stated to have limited periods of validity or be subject to periodic reconfirmation by the CA, and by having Alice check the certificate revocation list (CRL) maintained by the CA to warn recipients of certificates known to be no longer reliable. The absence of either rules or usages of trade determining who has a continuing duty to monitor the accuracy of data in certificate means that Alice has to make some difficult decisions. In addition to routinely checking the right CRL, Alice might decide that she will only accept certificates that state that their date of issue was within thirty days. If Alice is extremely cautious she can decide to accept only certificates that are very recent, maybe less than a day old, or even limit herself to certificates issued within minutes or microseconds. She still bears some risk, but it is reduced."86[169] Short life spans for public key certificates would also have the potential to change dramatically the relationship of the third party to the certification authority.
[170] It is reasonable to assume that the management of public keys will be assisted by computer software which will act as the interface between the certification authority, the subscriber and the third party. Even Pretty Good Privacy87 public key encryption software, for which there is no integrated third party public key management system, provides automated signature recognition and verification when the software is integrated into an e-mail program such as Pegasus Mail.88 Such a software interface could easily be configured to identify whether a public key certificate stored on the third party's public key ring was current at the time at which the third party proposed to rely upon it. If the software detected a stale-dated certificate, the software could display a prominent warning to the effect that the issuing certification authority declines any liability in relation to the certificate and that the certificate should be considered unreliable.
[171] We have seen how the third party is always the party who seeks to rely, possibly to his or her potential detriment, on the public key certificate. Precluding such reliance, or at any rate rendering such reliance unreasonable under the circumstances (such as where the third party is warned before-hand of the unreliable character of the certificate) effectively precludes liability on the part of the certification authority to the third party and is therefore an excellent hedge in favour of the certification authority against liability to the third party.
[172] To the extent that the third party then needs the assurance that reasonable reliance on a valid public key certificate affords, the third party could then be invited by the software program to pull a fresh certificate from the certification authority.
[173] The communications scheme would then look more like the following:
[174] Verification of incoming message with a pulled certificate89
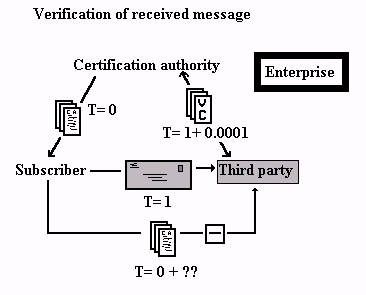
[175] The diagram above shows the following: in the beginning (time or "T" being equal to 0), the certification authority issues a public key certificate (the document with "ca" and the squiggles on it) to its subscriber. The public key certificate has a lifespan of hours at most. Some time later (we don't know exactly when, T= 0+??) the subscriber provides the public key certificate to the third party. Some time later still (T=1) the subscriber encrypts and signs a message which she sends to the third party. The third party then attempts to use the certificate to verify the digital signature of the subscriber prior to relying on its contents. The third party is then greeted with a prominent warning that the public key certificate is stale-dated and therefore unreliable and that for this reason it is impossible to verify the subscriber's digital signature (thus the break in the line between the third party and the public key certificate). The software then enquires as to whether the third party wishes to pull a certificate from the certification authority. Authorization is given by the third party and the software then polls the certification authority (at T=1+0.0001) for a verification certificate (the document with the letters 'vc' on it in the diagram) which itself has a very short validity period perhaps hours, even minutes. The third party is then able to verify the subscriber's certificate. The subscriber's employer ("enterprise" in the diagram) is not directly involved as a participant in this process, hence the Chinese wall drawn around the enterprise. As we have seen earlier, under existing standards and implementations, it is possible that the subscriber's authority or quality and capacity to bind her employer is attested to by the certification authority in the public key certificate.
[176] Encrypting an outgoing message with a pulled certificate
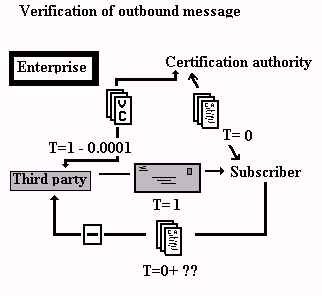
[178] Forcing the third party to pull the public key certificate from the certification authority creates an opportunity to allow the third party and the certification to form a relationship. That relationship can be readily framed in a contractual setting. The pull request coming from the third party to the certification authority constitutes a legally valid offer on the part of the third party which the certification authority can then accept. The exchange of the digital offer and the digital acceptance then forms a legally binding contract90 between the parties into which the certification authority's certification practice statement is incorporated by reference as we have seen earlier:
[179] "In general, computer-based mechanisms are probably sufficient to communicate offers and acceptances. For example, the Uniform commercial Code states that "[u]nless otherwise unambiguously indicated by the language or circumstances... an offer to make a contract shall be construed as inviting acceptance in any manner and by any medium reasonable in the circumstances."91 Computer-based acceptance of an offer to provide computer-related goods and/or services does not appear unreasonable in the abstract, and the clear trend is toward relying on these computer-based mechanisms for all communications purposes. This reliance seems natural given the widespread (and increasing) use of electronic data interchange and electronic mail, as well as the current and potential levels of trustworthiness of computer-based mechanisms. Accordingly the FCA would not foreclose the option of developing computer-based mechanisms to automate appropriate aspects of contract formation."92[180] From a purely technological point of view, opting for very short-lived public key certificates in a communications scheme which causes third parties to pull certificates from the certification authority could tend to pose a bandwidth problem over the network. For this reason, it may be necessary to consider a modification in the public key management protocols to provide for a different kind of certificate which we have called a verification certificate in the diagrams and accompanying text which illustrate our proposal for pulled certificates. Such verification certificates could be stripped down to a bare minimum to the extent that the underlying (but generally stale-dated and ineffective) public key certificate is still valid. The certification authority would not be required to convey all of the information normally found in the subscriber's public key certificate, only enough information to justify reliance on the existing certificate. The verification certificate would therefore be a kind of streamlined public key certificate which, when combined with the stale-dated public key certificate, would provide the third party with the information which his or her reliance on the subscriber's public key requires.
[181] The proposal to cause third parties to pull certificates certainly improves the efficiency of the public key infrastructure both in terms of the allocation of risk and the management of risk. It is not however without its own set of concerns and legal problems. One will have to consider rather sensitive issues relating to the activity logs and data trails potentially left as a result of pulling the certificates. The following illustrates the potential problem:
[182] "If Company A sends a digitally signed message to Company B, Company B must verify the digital signature by connecting to a database, verifying the digital signature and making sure that Company A's certificate is not on a certificate revocation list. This process, of course, will leave electronic footprints. Could the manager of the database disclose the fact that A and B were corresponding? What if A and B were discussing a possible merger or other transaction with significant consequences in the securities markets? Similarly, could the database disclose to Joe Whistleblower's defence-contractor employer that Whistleblower was verifying digital signatures of a reporter from the New York Times? Could the database manager take note of the fact that subscriber C frequently corresponded with a cardiologist's office, and sell C's name, address, or other personal information to a drug company interested in marketing a new drug for heart patients?"93[183] The foregoing issues are certainly not limited to the situation where a third party pulls public key certificates from a certification authority's Web server, since they arise in almost every communications context on Internet. They are important issues and they will have to be satisfactorily addressed. Clearly, such data must be treated confidentially. The solution probably lies in large measure in the architectural implementation of the certification authority's information systems, partly in the desire of the certification authority to refrain from actions perceived to be abusive of the trust reposed in the certification authority by the public and perhaps eventually by the adoption of laws designed to ensure the privacy of citizens.94
[184] Economic consequences of a distributed key management architecture
[185] We began by identifying a series of features inherent in the currently proposed public key management protocols which we felt militated against an efficient risk management model for a public key management service:
[197] In an implementation of such a system, it is the party who either generates the risk or the party who suffers the risk who is given a role to play and a tool with which to manage the risk. Thus:
[214] Verification
of an incoming message with a pulled certificate and enterprise credential
management
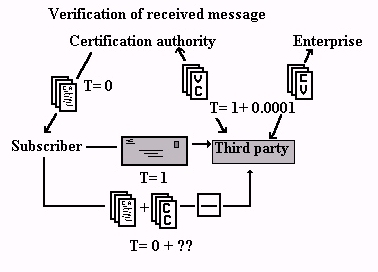
[215] In the beginning (time or "T" being equal to 0), the certification authority issues a public key certificate (the document with "ca" and the squiggles on it) to its subscriber. At some time thereafter the subscriber receives a credential certificate from his employer ('enterprise' in the diagram). Both the public key certificate and the credential certificate have a lifespan of hours at most. Some time later (we don't know exactly when, T= 0+??) the subscriber provides both the public key certificate and the credential certificate to the third party. Some time later still (T=1) the subscriber encrypts and signs a message which she sends to the third party. The third party then attempts to use the certificate to verify the digital signature of the subscriber prior to relying on its contents. The third party is then greeted with a prominent warning that the public key certificate and the credential certificate are stale-dated and therefore unreliable and that for this reason it is impossible to verify the subscriber's digital signature (thus the break in the line between the third party and the public key certificate). The software then enquires as to whether the third party wishes to pull fresh certificates from the certification authority and the enterprise. Authorization is given by the third party and the software then polls the certification authority for a verification certificate (at T= 1+ 0.0001) (the document with the letters 'vc' on it in the diagram) and the enterprise for a credential verification (the document with the 'cv' on it in the diagram), both these certificates having a very short validity period perhaps hours, even minutes. The third party is then able to verify the subscriber's signature, including the subscriber's authority to act for the enterprise. The subscriber's employer is now directly involved as a participant in this process and now manages its own risk in relation to the authority its employee exercises on its behalf.
[216] Encrypting an outgoing message with a pulled certificate and enterprise credential management
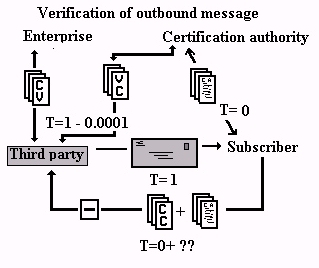
[217] In
the beginning (time or "T" being equal to 0), the certification authority
issues a public key certificate (the document with "ca" and the squiggles
on it) to its subscriber. At some time thereafter the subscriber receives
a credential certificate from her employer ('enterprise' in the
diagram). Both the public key certificate and the credential certificate
have a lifespan of hours at most. Some time later (we don't know exactly
when, T= 0+??) the subscriber provides the public key certificate and the
credential certificate to the third party. At some even later time
(T=1) the third party intends to encrypt and sign a message to be sent
to the subscriber. The third party therefore previously attempts to use
the subscriber's public key certificate to verify the subscriber's public
key prior to using the public key to encrypt the message. The third party
also attempts to verify the subscriber's credentials with the credential
certificate. The third party is then greeted with a prominent warning
that the public key certificate and the
credential certificate are
stale-dated and therefore unreliable and that for this reason it is impossible
to reliably use the certificates to encrypt the message (thus the break
in the line between the third party and the certificates). The software
then enquires as to whether the third party wishes to pull fresh
certificates from the certification authority and the enterprise. Authorization
is given by the third party and the software then polls the certification
authority for a verification certificate
[218] (at
T=1-0.0001) (the document with the letters 'vc' on it in the diagram) and
the enterprise for a credential verification (the document with
the 'cv' on it in the diagram), both these certificates having a very short
validity period perhaps hours, even minutes. These certificates are effectively
pulled
from the certification authority by the third party. The third party is
then able to reliably encrypt the message which is then sent to the subscriber
at T=1. The subscriber's employer is now directly involved as a participant
in this process and now manages its own risk in relation to the authority
its employee exercises on its behalf.
[219] Conclusion
[220] Efforts to develop the global information infrastructure must rely on the implementation of a ubiquitous global public key infrastructure. The implementation of such an infrastructure itself depends on the existence of underlying communications and technology protocols which give rise to, and even foster, an economic model which permits the parties intended to be served by the infrastructure not only to manage efficiently the risks to which they are subject, but which also parallels the existing paradigms to which they are already accustomed as closely as possible.
[221] The authors submit that the proposals which are outlined in this paper contribute to refining the currently proposed protocols in a way which permits a more efficient economic model to be created for the deployment of just such a global public key infrastructure.
German Digital Signature Act, Article 3 of the Federal Bill Establishing the General Conditions for Information and Communications Services, available at http://www.iid.de/rahmen/iukdge.html.
Draft IT legislation being contemplated in Massachusetts, http://www.magnet.state.ma.us/itd/legal
Quebec Notarial Act, R.S.Q. c. N-2
Quebec Civil Code
United States National Archives and Records Administration, http://www.nara.gov.
Utah Digital Signature Act (Utah Code Annotated Title 46, Chapter 3 (1996))
Quebec Act for the protection of personal information in the private sector R.S.Q. c. P-39.1.
Publications
American Bar Association, Section of Science and Technology, Information Security Committee, Digital Signature Guidelines, August 1, 1996.
I'Anson, C., and Mitchell, C. Security Defects in Recommendation X.509 - The Directory and Authentication Framework in Computer Communications Review, vol. 20, pp. 30-34 (1990).
Theodore Sedgwick Barrassi, The Cybernotary: Public key registration and certification and authentication of international legal transactions, text of a conference given at the 1996 RSA Data Security Inc. annual symposium, January 17th, 1996, on file with the authors.
Michael Baum, Federal Certification Authority Liability and Policy - Law and policy of certificate- based public key and digital signatures, U.S. Department of Commerce, National Technical Information Service, Gaithersburg, Maryland, June 1994, ISBN 1-886843-00-7.
Michael Baum and Henry Perritt jr. Electronic Contracting, Publishing and EDI Law, Wiley, 1991.
Karim Benyekhlef Les transactions dématé rialisées sur les voies électroniques: panorama des questions juridiques, in Les Autoroutes électroniques - usages droit et promesses, Les Éditions Yvon Blais Inc., 1995 at p. 115 and following;
C. Bradford Biddle Misplaced Priorities: The Utah Digital Signature Act and Liability Allocation in a Public Key Infrastructure, Volume 33 San Diego L. Rev. (forthcoming January 1997) and available on the Web in an earlier edition at http://www.SoftwareIndustry.org/issues/1digsig.html.
Blaze, M, Feigenbaum, J, & Lacy, J. Decentralized Trust Management., Proc. IEEE Conference on Security and Privacy, Oakland, California, May 1996.
Peter Blume Information Infrastructure and Data Protection. The Danish Perspective, International Journal of Law and Information Technology, Vol 4 No. 1, p. 1 at p. 16.
Amelia Boss, It ain't just a matter of security, speech given at a symposium entitled Doing Business Securely on the Information Highway, held in Montreal on August 30, 31 1995 sponsored by the Electronic Commerce World Institute and the Public Law Research Centre of the University of Montreal. A copy is on file with the authors.
Amelia Boss, The Emerging Law of International Electronic Commerce, (1992) 6 Temple Int'l & Comp. L. J. 293.
Robert Cassius de Linval, Le secret professionnel empêche-t-il l'utilisation du courrier électronique? in CyberNews, Volume II, No. III, Spring, 1996 at http://www.droit.umontreal.ca/CRDP/CyberNews/.
Jean-Pierre Chamoux, Réglementation et évolution technologique: de l'objet fuyant de la réglementation, speech given during a symposium on Internet regulation sponsored by the Public Law Research Centre of the University of Montreal and the Centre Jacques Cartier at Montreal in October 1996, on file with the authors.
P. Dodd and D.R. Bennett Waiver of Privilege and the Internet, (1995) 53 The Advocate 365.
Michael Erdle Legal Issues in electronic commerce 12 C.I.P.R 251.
Federal Government of Canada A survey of Legal Issues relating to the Security of Electronic Information, Information Technology Security Strategy Steering Committee, Legal Issues Working Group, June 1995, prepared for the Federal Treasury Board of Canada, p. 10-16. This document is also available in English and French at http://canada.justice.gc.ca/index_en.html.
Warwick Ford, Advances in Public-key Certificate Standards, 1995.
Warwick Ford, Computer Communications Security: Principles, Standard Protocols & Techniques (1994).
Michael Froomkin, The essential role of trusted third parties in electronic commerce 75 Oregon L. Rev. 49 (1996) available online at http://www.law.miami.edu/~froomkin/articles/trusted.htm .
Sunny Handa and Marc Branchaud, Re-Evaluating proposals for a Public Key Infrastructure in WJA Law Tech. vol. 29, No. 3, p. 1.
R.L. Jones, A lawyer's Duties with regard to Internet E-Mail, p.16 (student paper, August 6th 1995, Georgia State University College of Law in Atlanta. Available at http://www.gsu.edu/~lawppw/lawand.papers/bjones.html.
Hugh Lofting, The Story of Doctor Dolittle: being the history of his peculiar life at home and astonishing adventures in foreign parts with an introduction to the Canadian edition by Hugh Walpole, Toronto, McClelland and Stewart, 1923. < P > David Masse Le cadre juridique en droit civil québécois des transactions sur l'inforoute, (1997) 42 McGill L.J. (forthcoming January 1997), also available in an earlier edition among the conference materials for the 1995 AQDIJ symposium at http://www.juris.uqam.ca/aqdij.
Mitchell, C., Walker, M, and Rush, D. CCITT/ISO Standards for Secure Message Handling in IEEE Journal on Selected Areas in Communications, vol. 7, pp. 517-524 (1989).
Henry H. Perritt jr. Law and the Information Superhighway, John Wiley & Sons Inc., New York, 1996.
R.L. Rivest and B. Lampson, SDSI A Simple Distributed Security Infrastructure, Online working version 1.1 at http://theory.lcs.mit.edu/~rivest.
Pierre Trudel, Guy Lefebvre and Serge Parisien La preuve et la signature, Les publications du Québec, 1993.
Don Tapscott and Art Caston, Paradigm Shift, The New Promise of Information Technology, McGraw Hill, New York, 1993.
Verisign Inc., Certification Practice Statement, available at http://www.verisign.com/repository/CPS/CPSCH5.HTM.
Verisign Inc., Interfacing to VeriSign Digital ID Enrollment Services, available at http://www.verisign.com.
Benjamin Wright, The law of Electronic Commerce, Little Brown and Company, 1995, chap. ET1, Legal Identity and Signatures on the Information Highway, p. ET1:6.
P. Zimmermann. PGP User s Guide. MIT Press, Cambridge, 1994.
Protocols and Standards
Appendix B to ANSI standard x9.57 entitled Alternative Trust Models, Accredited Standards Committee X9, Financial Services, American Bankers' Association. A final draft is expected in February 1997.
IETF-PKIX documentation: the most current as of this writing draft-RFC as work in progress can be found at http://www.ietf.org under the title draft-ietf-pkix-ipki-part1-02.txt.
International Telegraph and Telephone Consultative Committee (CCITT). The Directory Authentication Framework, Recommendation x.509. 1993 update.
RFCs describing Privacy Enhanced Mail (PEM), an X.509 descendant, contained in RFCs 822, 1255, 1421, 1422, 1423, 1424, 1521, and 1847.
SSL Protocol, version 3.0. Available at http://home.netscape.com.
(2) (back to text at note2) Lawyer and partner, Chait Amyot, Montreal, Quebec, Canada - http://www.masse.org/., david@masse.org.
(3) (back to text at note3) Information security consultant, Cryptonym Corporation, Mississauga, Ontario, Canada, andrew@cryptonym.com.
(4) (back to text at note4) This article features paragraph numbering designed to simplify citation for onlinepublication. References in the table of contents of this article are therefore to paragraph numbers as well as to page numbers, the paragraph references being the numbers in square brackets. Cross-references to paragraphs within this paper are preceded by the symbol "P".
(5) (back to text at note5) Attributed to United States Vice-president Al Gore. See for instance http://metalab.unc.edu/nii/goremarks.html.
(6) (back to text at note6) http://nii.nist.gov/nii/niiinfo.html.
(7) (back to text at note 7) For materials on such initiatives see http://www.gii.org/
(8) (back to text at note 8) See for example the description of the health care sector information infrastructure proposed in Denmark in: Peter Blume Information Infrastructure and Data Protection. The Danish Perspective, International Journal of Law and Information Technology, Vol 4 No. 1, p. 1 at p. 16.
(9) (back to text at note 9) Benjamin Wright, The law of Electronic Commerce, Little Brown and Company, 1995, chap. ET1, Legal Identity and Signatures on the Information Highway, p. ET1:6.
(10) (back to text at note 10) R.L. Jones, A lawyer's Duties with regard to Internet E-Mail, p.16 (student paper, August 6th 1995, Georgia State University College of Law in Atlanta. Available at http://www.gsu.edu/~lawppw/lawand.papers/bjones.html; P. Dodd and D.R. Bennett Waiver of Privilege and the Internet, (1995) 53 The Advocate 365; Robert Cassius de Linval, Le secret professionnel empêche-t-il l'utilisation du courrier électronique? in CyberNews, Volume II, No. III, Spring, 1996 at http://www.droit.umontreal.ca/CRDP/CyberNews/.
(11) (back to text at note 11) Michael Froomkin, The essential role of trusted third parties in electronic commerce 75 Oregon L. Rev. 49 (1996) available online at http://www.law.miami.edu/~froomkin/articles/trusted.htm; Henry H. Perritt jr. Law and the Information Superhighway, John Wiley & Sons Inc., New York, 1996; Benjamin Wright, Op. Cit.,; Michael Erdle Legal Issues in electronic commerce 12 C.I.P.R 251.
(12) (back to text at note 12) Karim Benyekhlef Les transactions dématérialisées sur les voies électroniques: panorama des questions juridiques, in Les Autoroutes électroniques - usages droit et promesses, Les Éditions Yvon Blais Inc., 1995 at p. 115 and following; Pierre Trudel, Guy Lefebvre and Serge Parisien La preuve et la signature, Les publications du Québec, 1993; David Masse Le cadre juridique en droit civil québécois des transactions sur l'inforoute, (1997) 42 McGill L.J. (forthcoming January 1997), also available in an earlier edition among the conference materials for the 1995 AQDIJ symposium at http://www.juris.uqam.ca/aqdij.
(13) (back to text at note 13) Private keys also require management services. Such private key management services are beyond the scope of this article though they are touched upon to the extent that the methods used for the management of public keys have an impact on the management of private keys. Private key management services include vaulting private keys on smart cards and key escrow services intended for benefit of the key owner. See P212.
(14) (back to text at note 14) International Telegraph and Telephone Consultative Committee (CCITT). The Directory Authentication Framework, Recommendation x.509. 1993 update.
(15)(back to text at note 15) P. Zimmermann. PGP User s Guide. MIT Press, Cambridge, 1994.
(16) (back to text at note 16) R.L. Rivest and B. Lampson, SDSI A Simple Distributed Security Infrastructure, Online working version 1.1 at http://theory.lcs.mit.edu/~rivest.
(17) (back to text at note 17) See supra at note 15.
(18) (back to text at note 18) See supra at note 14.
(19) (back to text at note 19) The SSL Protocol, version 3.0. Available at http://home.netscape.com.
(20) (back to text at note 20) The most current as of this writing draft-RFC as work in progress can be found at http://www.ietf.org under the title draft-ietf-pkix-ipki-part1-02.txt.
(21) (back to text at note 21) Verisign currently makes use of x.509 v.2. See http://www.verisign.com.
(22) (back to text at note 22) See note 20 - the draft ietf ipki-pxix document
(23) (back to text at note 23) PKIX.
(24) (back to text at note 24) See supra at note 16.
(25) (back to text at note 25) Blaze, M, Feigenbaum, J, & Lacy, J. Decentralized Trust Management. Proc. IEEE Conference on Security and Privacy, Oakland, California, May 1996.
(26) (back to text at note 26) In other contexts in this paper we refer to the holder of the public key in the context of a public key infrastructure as a "subscriber". The use of the term principal in this section is unique in that it refers not to the end user of the protocol, but to the public key itself since, from a strictly computational point of view, one cannot tell from whom a message arrives. In a rigorous sense, you can only know that a message came signed by a particular public key. In the end, the only identity that can be ascribed to the message without question is the identity of the key itself.
(27) (back to text at note 27) Rivest, R. L. and Lampson, B. Ibid.
(28) (back to text at note 28) Rivest, R.L. and Lampson, B. Ibid.
(29) (back to text at note 29) Warwick Ford, Advances in Public-Key Certificate Standards, 1995.
(30) (back to text at note 30) Verisign Inc., Verisign Certification Practice Statement, 8.1, http://www.verisign.com/repository/ CPS/CPSCH8.HTM.
(31) (back to text at note 31) This is only true as far as you can trust people to keep up to date with key compromise notifications.
(32) (back to text at note 32) In the current technological context, this could extend from a simple local or wide area network or intranet, to an extranet or a relatively large virtual private network.
(33) (back to text at note 33) In the current technological context, this would mean parties who do not participate in the same local or wide area network, intranet, extranet or virtual private network
(34) (back to text at note 34) The protocols refer to certification policy statements whereas the Digital Signature Guidelines refer to certification practice statements. See American Bar Association, Section of Science and Technology, Information Security Committee, Digital Signature Guidelines, August 1, 1996, Guideline 1.8 under the heading Related Terms at p. 32.
(35) (back to text at note 35) Ibid. note 1.8.1 at p. 33.
(36) (back to text at note 36) See the discussion below concerning the management of risk in the relationship between the relying party and the certification authority at P128 and following.
(37) (back to text at note 37) Michael Baum, Federal Certification Authority Liability and Policy - Law and policy of certificate-based public key and digital signatures, U.S. Department of Commerce, National Technical Information Service, Gaithersburg, Maryland, June 1994, ISBN 1-886843-00-7, chapter VI Legal considerations, at pages 79 and following; Michael Froomkin, Op. cit.
(38) (back to text at note 38) C. Bradford Biddle Misplaced Priorities: The Utah Digital Signature Act and Liability Allocation in a Public Key Infrastructure, Volume 33 San Diego L. Rev. (forthcoming January 1 9 9 7 ) and available on the Web in an earlier edition at http://www.SoftwareIndustry.org/issues/1digsig.html; Michael Froomkin Op. cit. at p. 83 under the heading The difficulty of Identifying the Rights and Duties of Private Certification Authorities.
(39) (back to text at note 39) The term "paradigm shift" has been popularized to signify a fundamental change in the way in which a process is carried on. Here we refer to the transposition of paper-based communications to a digital medium. For a detailed etymology of the phrase see Don Tapscott and Art Caston, Paradigm Shift, The New Promise of Information Technology, McGraw Hill, New York, 1993, at pages xi to xiv.
(40) (back to text at note 40) This statement overstates, at least as regards the laws in force in the Province of Quebec which is a civil law jurisdiction, the importance of notarial practice. Notaries in Quebec are legal professionals whose training and expertise equals that of lawyers though they are not qualified to act as barristers. It is only a very small class of transactions which requires the intervention of a notary, restricted to hypothecs (mortgages) on immovable (real) property, hypothecs (mortages) securing the payment of bonds or negotiable instruments, marriage contracts (pre-nuptial agreements) and certain gifts of property. The enforceability of the vast majority of commercial transactions does not depend in any way on the intervention of a notary and notaries do not in fact play an important role in the majority of commercial transactions in Quebec. They do however act as conveyancers in the overwhelming majority of transfers, sales and financings of immoveable (real) property in Quebec. In cases where a notarial act en minute is a formal requirement, the satisfaction of that requirement presently requires the personal presence of the signatories before a notary who is a member in good standing of the L'Ordre des Notaires du Québec (Quebec Notarial Act, R.S.Q. c. N-2). Foreign notaries licensed in other civil law jurisdictions have no standing to receive notarial acts for the purposes of Quebec legal requirements. As regards the source of the legal requirements as to the form of the few particular transactions which are subject to the requirement of the notarial act en minute, they are found in the Quebec Civil Code:
"Art. 440: Marriage contracts shall be established by a notarial act en minute, on pain of absolute nullity.(41) (back to text at note 41) Theodore Sedgwick Barrassi, The Cybernotary: Public key registration and certification and authentication of international legal transactions, text of a conference given at the 1996 RSA Data Security Inc. annual symposium, January 17th, 1996, on file with the authors.Art. 1824: The gift of movable or immovable property is made, on pain of absolute nullity, by notarial act en minute, and shall be published.
These rules do not apply where, in the case of the gift of movable property, the consent of the parties is accompanied by delivery and immediate possession of the property.
Art. 2692: A hypothec securing payment of bonds or other titles of indebtedness issued by a trustee, a limited partnership or a legal person authorized to do so by law shall, on pain of absolute nullity, be granted by notarial act en minute in favour of the person holding the power of attorney of the creditors.
Art. 2693: An immovable hypothec is, on pain of absolute nullity, granted by notarial act en minute."
(42) (back to text at note 42) Amelia Boss, The Emerging Law of International Electronic Commerce, (1992) 6 Temple Int'l & Comp. L. J. 293, at pp. 300 and following.
(43)
(back
to text at note 43) The authors owe the juxtaposition of the concepts
of pyramids and geodesic domes as they relate to Internet and telecommunications
companies to a speech given by professor Jean-Pierre Chamoux of Université
de Marne-la-Vallée entitled
Réglementation et évolution
technologique: de l'objet fuyant de la réglementation, during
a symposium on Internet regulation sponsored by the Public Law Research
Centre of the University of Montreal and the Centre Jacques Cartier.
Prof. Chamoux wrote:
"Internet introduit, sur une échelle internationale qui échappe au contrôle politique des réglementations nationales, un nouveau paradigme: celui des réseaux géodésiques, échappant aux hiérarchies pyramidales du téléphone, aussi bien par leur ingénirie que par leur routage ou par leur addressage!" [translation by the authors: Internet introduces, on an international scale a new paradigm which defies the political control of national regulation: that of geodesic networks, which defy the pyramidal hierarchies of telephony, as much by virtue of their engineering as by virtue of their routing and addressing!](44) (back to text at note 44) See supra at note 14.
(45) (back to text at note 45) See supra at 36 and following. See as well the IETF-PKIX documentation; RFC's describing Privacy Enhanced Mail (PEM), an X.509 descendant, contained in RFCs 822, 1255, 1421, 1422, 1423, 1424, 1521, and 1847; Mitchell, C., Walker, M, and Rush, D. CCITT/ISO Standards for Secure Message Handling in IEEE Journal on Selected Areas in Communications, vol. 7, pp. 517-524 (1989); I Anson, C., and Mitchell, C. Security Defects in Recommendation X.509 - The Directory and Authentication Framework in Computer Communications Review, vol. 20, pp. 30-34 (1990); Sunny Handa and Marc Branchaud, Re-Evaluating proposals for a Public Key Infrastructure in WJA Law Tech. vol. 29, No. 3, p. 1 at p. 11.
(46) (back to text at note 46) The representation of internet addresses as dotted quads (such as 192.206.114.28) may give the impression that the organization of the Internet is far more hierarchical than it really is. Breaking up the total address space into different size-classes of network as well as the careful management of the routing tables to direct the IP traffic, allow Internet to retain the efficiency of a hierarchical network, all the while lending a large degree of resiliency and robustness to the entire network. In this way large subnets of the Internet can sporadically fail without a material adverse consequence to the entire network. From an end user perspective, the domain name service (DNS) flattens the hierarchy out even more: the entire virtual world is divided into a few broad categories (commercial, organizations, educational institutions, network providers, and countries) and then the individual unit; it takes no great syntactic or semantic parsing to understand by whom the domain ibm.com is administered. On an interesting but admittedly circumstantial note, it is precisely those areas of Internet administration that depend on hierarchical data structures where the Internet is seen to have its most immediate problems: (a) Internet is rapidly running out of network addresses forcing the adoption of inefficient ad hoc solutions until IPv6 becomes widespread, and (b) we are rapidly approaching the point where the few top-level domain names .com , .gov , .net , .org and the like are no longer sufficient for continued use (see http://www.alternic.net for an example). One of the more potentially memorable examples of this was when the domain name peta.org was denied to the organization People for the Ethical Treatment of Animals since it had already been registered... to someone hosting a website entitled People Eating Tasty Animals Many people feel that this sort of situation, while not critical now, will probably have to be resolved in a different manner in the future.
(47) (back to text at note 47) ; Michael Froomkin, Op Cit. at page 57 citing Warwick Ford Looking into the crystal Ball: Certificates revisited a presentation given at a symposium in 1995 in which Dr. Ford suggested that the organization of certification authorities in rigid hierarchies was not an appropriate model for a large scale deployment of a public key infrastructure; see also Warwick Ford, Advances in Public-key Certificate Standards, 1995; Sunny Handa and Marc Branchaud Op. Cit. at p. 11.
(48) (back to text at note 48) Michael Froomkin, Op Cit. at page 56.
(49) (back to text at note 49) Digital Signature Guidelines, August 1, 1996, note 34 at p. 15:
"A number of models exist which implement different strategies for the certification of the public keys of certification authorities who issue certificates (sometimes referred to as "issuing authorities"). Some examples include (i) a multi-level hierarchical structure back to a single "root", where public keys of issuing authorities are certified by the next higher-level certification authority; (ii) a flatter hierarchical structure where a single "root" might directly certify the public keys of all issuing authorities below it; (iii) a single level of issuing authorities which "cross-certify" each others' public keys; or (iv) a system in which each issuing authority's public key is certified in some reliable manner without reference to a second certification authority. In a hierarchical system, the public key of the "root" certification authority is, by definition, self-authenticating."The Utah Digital Signature Act (Utah Code Annotated Title 46, Chapter 3 (1996)) which may to a certain extent be viewed as a model digital signature law, contemplates a relatively flat hierarchy under which the Utah Department of Commerce, Division of Corporations and Commercial Code certifies all certification authorities licensed to operate in the state (103(11), 104 and 201).
(50) (back to text at note 50) For an excellent description of the two alternative types of certification hierarchies refer to draft Appendix B to ANSI standard x9.57 entitled Alternative Trust Models, Accredited Standards Committee X9, Financial Services, American Bankers' Association. A final draft is expected in February 1997.
(51) (back to text at note 51) Amelia Boss, It ain't just a matter of security, speech given at a symposium entitled Doing Business Securely on the Information Highway, held in Montreal on August 30, 31 1995 sponsored by the Electronic Commerce World Institute and the Public Law Research Centre of the University of Montreal. A copy is on file with the authors.
(52) (back to text at note 52) Or of the enterprise issuing a credential certificate. For the question of the issuance of credential certificates, see 126 below.
(53) (back to text at note 53) http://www.lycos.com.
(54) (back to text at note 54) http://infoseek.go.com.
(55) (back to text at note 55) http://www.altavista.com/.
(56) (back to text at note 56) See for example Baum Op. cit. p. 64 C.4 Attribute and Other Certificates, particularly note 152, and p. 55 note 132.
(57) (back to text at note 57) For brevity's sake we will only refer to persons, but the reader should understand that the discussion applies equally to other persons such as corporations and to other entities such as partnerships, syndicates, unions, foundations, trusts, as well as potentially to inanimate objects or processes (such as applications where data sent by digital surveillance cameras in a closed circuit security system is encrypted by a public key assigned to the camera), etc., etc.
(58) (back to text at note 58) The information and graphic images reproduced below were obtained from the Web site of the United States National Archives and Records Administration, http://www.nara.gov.
(59) (back to text at note 59) We prefer to use the term 'public key management service' to the term 'certification authority' because we feel that it reflects more accurately the nature of the activities carried on. Depending on the context from time to time, we may also refer to this entity as a 'certification authority'. In either case, the reference is to the entity which serves the role of linking entities to their public keys.
(60) (back to text at note 60) For a glimpse of the extent to which even simple identification of a person on the basis of static information may prove to be a challenge, see Michael Baum, Op. cit. at page 48, note 117.
(61) (back to text at note 61) Bankers Trust affiliate Certco, IBM, GTE, Verisign Inc., comprise the U.S. market for commercial public key management services at this time: Information Week, E-commerce gets real, December 9th, 1996. In Canada, the Stentor alliance of telecom companies offers public key management services under the name OnWatch. The Bell Sygma OnWatch service is described at http://www.public-key.com/index.html.
(62) (back to text at note 62) Verisign Inc., Verisign Certification Practice Statement, 2.3.4, http://www.verisign.com/repository/ CPS/CPSCH2.HTM.
(63) (back to text at note 63) Digital Signature Guidelines, comment 1.5.3 at page 30:
"A certificate will generally take the form of the binary records common in current electronic data interchange ("EDI"). A certificate will usually be in the form prescribed by International Telecommunications Union ("ITU") (formerly International Consultative Committee on Telephony and Telegraphy, "CCITT") Standard x.509 v.3, but any certificate meeting the requirements of this Guideline 1.5 (certificate) is acceptable. The use of additional fields and extensions to provide additional attributes or information (e.g. authorization of the subscriber as an agent, or cross-reference to other databases providing information about the subscriber) is optional."Refer as well to the Utah Digital Signature Act, Utah Code Annotated Title 46, Chapter 3 (1996) at 103(3).
(64) (back to text at note 64) Hugh Lofting, The Story of Doctor Dolittle: being the history of his peculiar life at home and astonishing adventures in foreign parts with an introduction to the Canadian edition by Hugh Walpole, Toronto, McClelland and Stewart, 1923.
(65) (back to text at note 65) For the purposes of this section the authors revert to the term 'certification authority' to describe the public key management service in order to make the authors' proposal relating to the dissemination of public key certificates as easy to relate as possible to the currently accepted scheme of public key management.
(66) (back to text at note 66) Federal Government of Canada A survey of Legal Issues relating to the Security of Electronic Information, Information Technology Security Strategy Steering Committee, Legal Issues Working Group, June 1995, prepared for the Federal Treasury Board of Canada, p. 10-16. This document is also available in English and French at http://canada.justice.gc.ca/index_en.html.
(67) (back to text at note 67) Michael Baum, Op. Cit. page 62, note 148.
(68) (back to text at note 68) Ibid. page 74.
(69) (back to text at note 69) One can imagine an infinite set of circumstances running from failure to complete the certification process in a timely manner to liability to the subscriber who slips and falls on his way into the lobby.
(70) (back to text at note 70) Ibid. pages 79 and following; Michael Froomkin, Op. Cit. at pages 83 and following; Sunny Handa and Marc Branchaud Op. Cit.; C. Bradford Biddle Op. cit.
(71) (back to text at note 71) See supra at 136.
(72) (back to text at note 72) Michael. Baum, Op. Cit. pages 98, 83 and following under the heading B. Legal infrastructure of the FCA. In jurisdictions which have adopted digital signature legislation, the legislation plays an important role in allocating risk and liability among the parties active in a public key infrastructure. For a detailed discussion of the allocation of such risks as between the certification authority and subscribers under the Utah Digital Signature Act (Utah Code Annotated 46-3-101 to 46-3-504) see C. Bradford Biddle Op. Cit.
(73) (back to text at note 73) Digital Signature Guidelines, August 1, 1996, 1.8 Certification practice statement and the comments thereunder, particularly 1.8.3 concerning the principle of incorporation by reference of the certification practice statement in the contract between the certification authority and the subscriber.
(74) (back to text at note 74) C. Bradford Biddle Op. Cit. at p. 54 of the draft paper.
(75) (back to text at note 75) For a detailed discussion the reader should refer to Michael Froomkin, Op. Cit. section III A 2 entitled Misrepresentation whether wilful or negligent of CA's client, not detected by CA, at pages 91 and following. For a Canadian perspective see Sunny Handa and Marc Branchaud Op. Cit. at p. 21 and following; See also Michael S. Baum, Op. Cit. at pages 95 and following under the heading Recipient v, CA - Tort Liability and pages 97 and following under the heading Recipient v. CA - Contract Liability.
(76) (back to text at note 76) Michael Froomkin, Op. Cit. at page 95.
(77) (back to text at note 77) Ibid. at page 98.
(78) (back to text at note 78) Utah Digital Signature Act, Utah Code Annotated Title 46, Chapter 3 (1996), Part 3 Duties of Certification Authorities and Subscribers, 303.
(79) (back to text at note 79) See the excellent matrix developed by the Information Security Committee of the American Bar Association Science and Technology Section which sets out the status of legislative approaches to digital signatures and the admissibility of digital records generally athttp://state.ma.us/itd/legal/matrix10.htm.
(80) (back to text at note 80) See for instance the German Digital Signature Act, Article 3 of the Federal Bill Establishing the General conditions for Information and Communications Services, available at http://www.iid.de/rahmen/iukdge.html, formerly available in draft and unofficial form at http://ourworld.compuserve.com/homepages/ckuner/digsig.htm#German. France is also in the process of adopting digital signature legislation. Documents recently leaked from the government of France indicate that French law will likely require that all certification authorities and encryption algorithms be approved by the government of France and that all symmetric encryption keys and all private keys for asymmetric cryptosystems be escrowed with the certification authority. See http://www.club-internet.fr/planete/crypto/decret/.
(81) (back to text at note 81) Michael Froomkin, Op. Cit. at page 110 under heading III C 2 The case against legislation.
(82) (back to text at note 82) C. Bradford Biddle Op. Cit. at pp. 29 and following of the draft version of the paper.
(83) (back to text at note 83) Such as the draft legislation being contemplated in Massachusetts, http://www.magnet.state.ma.us/itd/legal.
(84) (back to text at note 84) Note that Verisign Inc. contemplates a minimum certificate operational period of one (1) year from the date of issuance. Verisign Certification Practice Statement, 8.8, http://www.verisign.com/repository/CPS/CPSCH8.HTM.
(85) (back to text at note 85) Comment of Robert R. Jueneman, Security Architect, Novell Information Security, Internet Infrastructure Division, concerning a proposed discussion draft of an initial report on digital signatures:
"It might be worth inserting a comment to the effect that there might or might not be any ind of a contractual relationship between the relying party and the CA who issued the ertificate, or perhaps between the relying party and his own CA, with whom he might have a contractual arrangement. I am inclined to believe that our current open-jawed triangle, the "widows and orphans" model of an uninvolved relying party, is not necessarily the best foundation for moving forward with electronic commerce. I would prefer a closed triangle or a quadrilateral (two CAs), where the subscriber and the relying parties would assume a degree of reciprocity in their actions when their respective CAs have cross-certified each other."E-mail posting to the CommerceNet E-payments list server dated December 3rd 1996, cited by the authors with permission from Robert Jueneman, a print-out of which is on file with the authors.
(86) (back to text at note 86) Michael Froomkin, Op. cit. at page 61. See also Utah Digital Signature Act, Utah Code Annotated Title 46, Chapter 3 (1996), Part 3 Duties of Certification Authorities and Subscribers, comment to 303, itself citing Warwick Ford, Computer Communications Security: Principles, Standard Protocols & Techniques (1994), p. 85.
(87) (back to text at note 87) http://web.mit.edu/network/pgp.html. [Ed.: It's now March 2018. That original link no longer works, the new link is now: https://pgp.mit.edu/] .
(88) (back to text at note 88) http://www.pegasus.usa.com.
(89) (back to text at note 89) The reader should bear in mind that the scenarios described below are intended only to illustrate the discussion and are not intended to describe in detail a fully-functioning proposal for a real-world implementation.
(90) (back to text at note 90) Henry H. Perritt jr. Op. Cit. at p. 379; Benjamin Wright, Op. Cit. chap. ET1, Legal Identity and Signatures on the Information Highway, p. 15:1; For a civil law perspective see David Masse, Op. Cit.
(91) (back to text at note 91) Citing U.C.C. 2-206; Restatement of Contracts (Second) (1981) 30; Michael Baum and Henry Perritt jr. Electronic Contracting, Publishing and EDI Law, Wiley, 1991 6.8.
(92) (back to text at note 92) Michael S. Baum, Op. Cit. page 88.
(93) (back to text at note 93) C. Bradford Biddle Op. Cit. at footnote 26, on p. 12 of the draft paper.
(94) (back to text at note 94) The province of Quebec is perhaps the only jurisdiction with laws which address specifically the right of the individual to the respect of personal privacy: Quebec Civil code, articles 35 to 41; Act for the protection of personal information in the private sector R.S.Q. c. P-39.1.
(95) (back to text at note 95) Note that Verisign Inc. indicates in its Certification Practice Statement that it does not monitor the correctness of statements in public key certificates on a ongoing basis, Verisign Certification Practice Statement, 5.1, http://www.verisign.com/repository/CPS/CPSCH5.HTM.